 NEWS
NEWS
 NEWS
NEWS
 NEWS
NEWS
It is a fun time to be in I.T since pretty much everything is changing under disruptive new technology trends. The world of identity is not indifferent to this change. New IT technology platforms such as cloud, mobile, and social are already impacting the way modern enterprises manage identities. Indeed, these changes are profound and will turn the world of identity upside down.
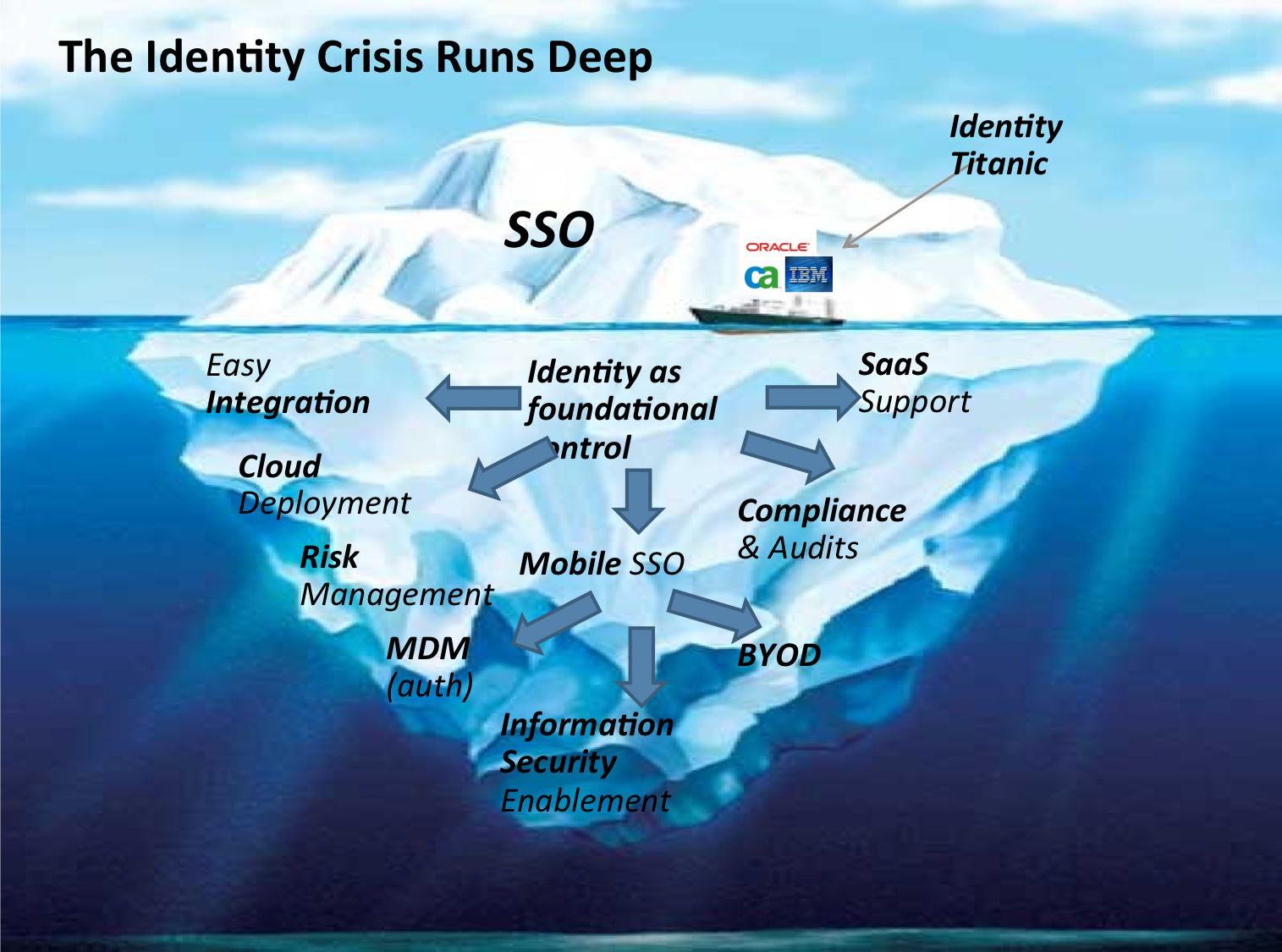
For most users, identity has an obvious manifestation: it is the sign-in experience (or lack there of). For I.T, login is an old problem. As the corporate world embraces more applications, both internal and external, the login user experience is increasingly becoming horrendous. The problem lies in the high visibility of the user interface. From the CEO, to executives, to front line employees, everyone can see when the sign-in experience is broken. Immediately, all fingers are pointing to IT as the obvious culprit. But did did not we address and solve the very same problem 10 years ago already? Have not all we bought and deployed CA Site Minder, Oracle Identity Manager or IBM Tivoli? Of course, we did; but the cloud came along and added a large number of new applications, breaking the old identity system that took so much time and pain to deploy in the first place.![]()
While the SSO problem resembles the proverbial iceberg, CIOs currently feel that they can sail right past it, as they are more worried about the daunting ice masses the likes of BYOD floating in the ocean of network security. Ironically, the SSO issue is looming high above the corporate information technology ship, certainly high enough for everyone on board to see. Yet none of us currently see the mass floating beneath the surface, so we feel that we can outmaneuver it–the tiny white SSO hurdle will undoubtedly be crushed. Pundits will say that enterprise already has all the tools on board to deal with this. And If it does not, employees can certainly handle a few more names and passwords and cope with a little loss of productivity. Full speed ahead, captain. I.T. has more urgent priorities than dealing with a mere user interface issue.
We are mistaken: The identity iceberg cannot be avoided. The main obstacle to the transformation of IT is perhaps the lack of a true reflection on the significance of
identity in the new world of cloud, mobile and social enterprises. CIOs and CISOs worldwide need to start integrating identity as a fundamental tenet of their I.T.
strategy. In the new world of modern I.T., identity becomes foundational. In fact, it may well be the last thing that IT can still control. What is core to IT tomorrow? Not user devices since they become unmanaged (BYOD); not the infrastructure since storage, computing and bandwidth become outsourced (IAAS); not the application since it is Software as a Service (SaaS) becomes mission-critical. Alongside information protection, identity is about to become core and strategic to IT’s own future. Therein lies the true lesson of the identity iceberg and its potential for an IT Titanic.
The wisdom of the iceberg is that the true danger lies below the surface. Although, SSO cannot be ignored, a successful identity strategy cannot be reduced to achieving a single login experience. Ignoring the user experience challenge of multi-application login is
certainly wrong. The proliferation of identities within enterprise can create an insurmountable obstacle towards the adoption of these new IT trends. However, the quest for SSO without understanding the additional need for identity as an integration, security, and enablement layer will prove even more shortsighted.
Identity becomes an integration layer. It must quickly integrate any application, whether a new SaaS, or a legacy Intranet app. And it must do so with minimal integration work for our IT staff (point and click, no coding). Identity must be about all users: employees of course, but also external users such as business partners, suppliers or customers. If IT is to ever IT becomes a business enablement function, we must learn to manage all user identities across all applications. The shift to the cloud is inexorable but the world of IT applications and users remains hybrid.
Without a true identity platform, security, risk management and compliance in the new world of IT will prove impossible. The new SSO creates a single front door to all corporate resources, both internal and external. If the SSO door is easy to open or compromise, our entire enterprise security collapses. But identity is also a security enabler. Today’s security policies are based on knowing who you are. If identities proliferate in the workplace, these policies become inconsistent at best, unenforceable at worst.
Identity becomes an essential security control. As IT relinquishes the control of user devices (BYOD) and the network (public IAAS cloud), bolstering the management and identification of users becomes a priority. To accept the flow of corporate information across devices and network that are no longer ours, we will need to trust our identities even more. In fact, identity and access control allows us to re-create a controlled information path even when the end points (device and applications) are no longer ours.
Identity is about enablement. Mobile users put a higher premium on user experience than anyone. Will mobile users tolerate multiple logins? Mobile Device Management (MDM) and Mobile Application Management (MAM) require identity too. Unmanaged mobile devices that live mostly outside our network will require strongly managed identities. Yesterday’s identity systems do not even know the word “mobile”.
Ultimately, the path to a cloud, mobile and social enabled enterprise begins with a comprehensive grasp of identity. In the same way Salesforce challenged the status quo of those who preceded them; identity as a service is about to redefine the way we manage users. Identity has never been more strategic. There is no future of IT without it;
period full stop. The alternative is the identity iceberg and we have all seen how the movie ends. The time has time to choose a modern and comprehensive identity system.
THANK YOU