 INFRA
INFRA
 INFRA
INFRA
 INFRA
INFRA
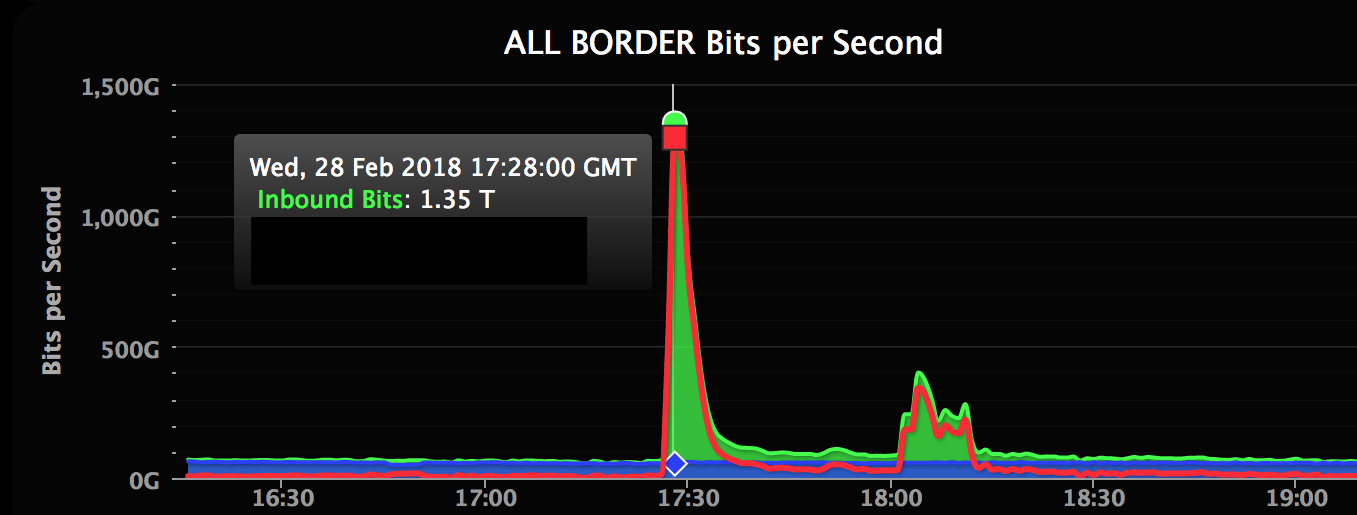
Days after security companies first detected a new form of distributed denial-of-service attack, GitHub has been targeted by the largest DDoS attack ever recorded.
Detailed in an incident report, the attack occurred at 12:21 p.m. EST Wednesday and also saw an amplification of the attack using the same new Memcached-based approach. The DDoS attack, which involves multiple computer systems flooding the target site with traffic, peaked at 1.35 terabytes per second, or 126.9 million packets per second.
After the data overwhelmed GitHub’s servers, causing them to stop responding, the company turned to Akamai to filter out the malicious traffic. Services resumed by 12:30 p.m.
When the method was first detailed, security researchers warned that attacks using Memcached would likely escalate. Now, enterprises are being told to be prepare in case they are attacked.
“While the DDoS attack GitHub experienced was the largest ever recorded, organizations should be prepared for campaigns of this magnitude going forward, as they’ll likely become commonplace,” Rod Soto, director of security research at JASK Inc., told SiliconANGLE. “DDoS attacks of 1TB or more will continue to surface as the prevalence of IoT devices in the home and the enterprise expands.”
As a result, he said, it’s crucial that the industry deploy the right monitoring capabilities to make it easier to track and mitigate the new vulnerabilities. “Until this happens, we should expect more potentially crippling DDoS campaigns exploiting IoT as a main attack vector,” he said.
Peter Martini, president and co-founder of iboss, noted that attackers will continue to find new and better ways to amplify DDoS attacks. “While there is little we can do to secure network infrastructure without massive investment, enterprises can ensure they are protected against these types of attacks by proactively deploying, cloud-based mitigation services that are capable of identifying and mitigating malicious DDoS traffic before it reaches their network,” Martini said.
NS1 Inc. Chief Executive Officer Kris Beevers said there’s a five-step process enterprise network administrators can implement now, if they haven’t already, to help mitigate DDoS attacks.
Step one is to deploy Domain Name System security extensions. “Cache poisoning, which redirects legitimate requests to malicious resources, is a common threat that has serious consequences for online enterprises and their customers,” Beevers said. “DNSSEC prevents attacks that can compromise the integrity of answers to DNS queries by cryptographically signing DNS records to verify their authenticity.”
Second, companies should get help managing their DNS.” “Managed DNS providers enable economies of scale,” Beevers explained. “Anycasted networks with points of presence around the world are far more powerful and reliable than trying to roll your own data centers. Borrow a page from the cloud computing playbook, and take advantage of DNS infrastructure through a managed DNS provider.”
Step three is to have multiple ways to avoid and recover from attacks. “Redundancy ensures resiliency from DDoS and other attacks,” Beevers said. “Secondary DNS does not mean you need a second provider, although it is certainly an option. Instead, it doubles the availability of DNS addresses through a secondary network.”
Fourth, businesses should enable two-factor authentication, which involves using not only a password but an additional factor such as something only the person can know or possesses, on management accounts. “Stronger security controls are only as strong as their weakest link, so be sure to control access to your security management accounts with two-factor authentication.”
Finally, and this gets a little more geeky, enterprises need to secure their secondary DNS. “If you are using zone transfers as part of your DNS setup, for example as part of a hidden master setup or in a primary+secondary configuration with two providers, ensure the integrity of the zone transfers by leveraging TSIG to sign the transfers with your private key, and limit exposed surface area by whitelisting the transfer IP addresses of your secondary providers.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.