Duncan Riley
Latest from Duncan Riley
DeNexus and Cipher team up to deliver enhanced risk assessment models for industrial cybersecurity
Cyber risk modeling for industrial networks company DeNexus Inc. today announced a new partnership with cybersecurity firm Cipher Security LLC to tackle operational technology and industrial control systems cyber risks in the realm of industrial and physical critical infrastructure. The collaboration between these two companies integrates advanced inside-out data from Cipher, encompassing vulnerabilities and critical ...
Secure remote access gets a boost with new Cyolo-TD SYNNEX partnership
Remote privileged access management company Cyolo Ltd. today announced a new partnership with information technology distribution company TD SYNNEX Corp. aimed at enhancing secure remote access solutions for industrial enterprises. Under the partnership, TD SYNNEX partners can offer their clients advanced secure remote access capabilities via Cyolo’s distributed Cyolo PRO platform. The platform enables service providers and IT ...
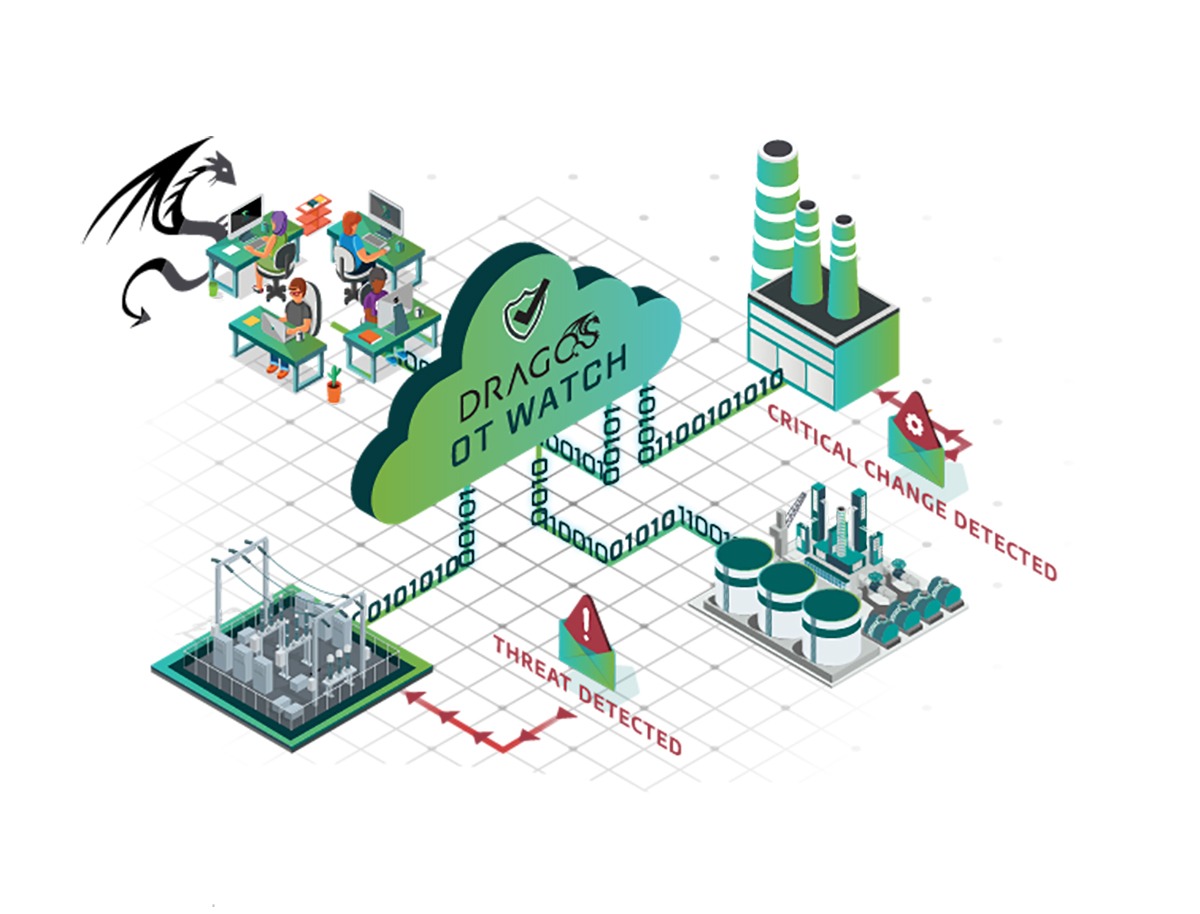
Swimlane and Dragos integrate platforms to improve threat detection in IT and OT environments
Low-code security automation company Swimlane LLC today announced a new partnership with industrial control system cybersecurity startup Dragos Inc. to extend protection for operational technology infrastructure with automation. The partnership launches with an integration between Swimlane Turbine and the Dragos Platform that allows customers to automate threat detection and enrichment across information technology and OT environments, leveraging artificial intelligence ...
Sophisticated software supply chain attack hits Top.gg, compromises GitHub accounts
Researchers at application security testing firm Checkmarx Ltd. today detailed a recently discovered software supply chain attack that targeted Top.gg, a popular search and discovery platform for Discord servers, bots and other social tools, along with individual developers on GitHub. The threat actors gained access using multiple tactics, techniques and procedures, including account takeover via stolen browser cookies, contributing ...
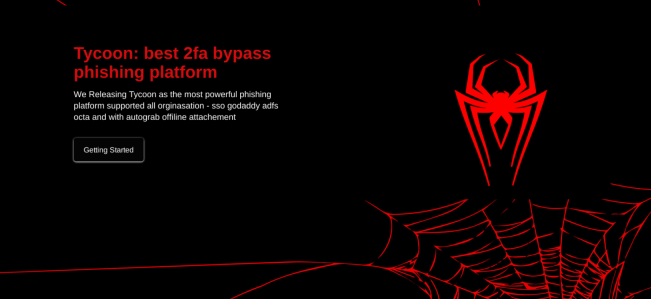
Newly detailed ‘Tycoon 2FA’ phishing kit bypasses multifactor authentication
Cybersecurity researchers at Sekoia ApS’ Threat Detection & Research team are warning of a new phishing kit linked to the adversary-in-the-middle technique that is being utilized by multiple threat actors to conduct effective attacks. Called “Tycoon 2FA,” the phishing kit has been active since at least August 2023 and is claimed to now be one ...
US and UK announce sanctions against alleged Chinese cyber espionage group APT 31
The U.K. and U.S. governments have announced sanctions against alleged Chinese hackers and the APT 31 threat group that was allegedly involved in hacking activities in both countries. The U.S. Department of the Treasury’s Office of Foreign Assets Control announced today that it had sanctioned Wuhan Xiaoruizhi Science and Technology Co. Ltd., an alleged China-based ...
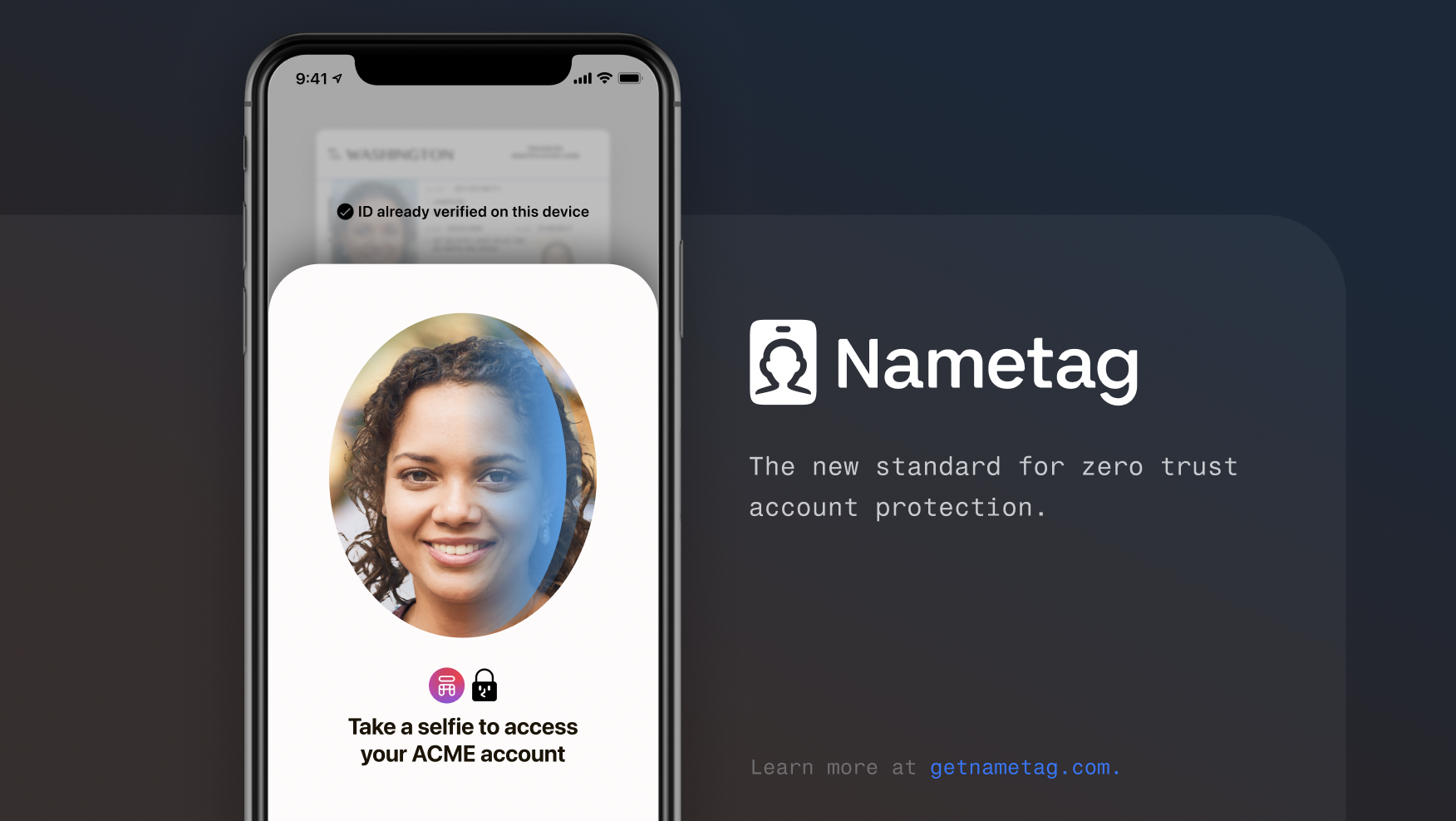
New solution from Nametag targets AI-generated deepfake security threats
Identity verification platform startup Nametag Inc. today announced the launch of a new self-service account recovery solution that prevents artificial intelligence-generated deepfake attacks. Called Nametag Autopilot, the new service has been designed to prevent social engineering and impersonation attacks while saving organizations millions by deflecting time-consuming password and multifactor authentication resets to self-service. The problem ...
Researchers uncover unfixable vulnerability in Apple CPUs affecting cryptographic security
A newly published paper from researchers details an unpatchable vulnerability in Apple Inc.’s M series of chips that allows attackers to extract secret keys used in cryptography operations. Dubbed GoFetch, the vulnerability can be exploited by a side-channel attack, which exploits indirect information to uncover secret data, such as cryptographic keys. In the GoFetch scenario, the method ...
AttackIQ’s Ready! 2.0 update enhances cyber defense with on-demand testing
Security optimization platform company AttackIQ Inc. today announced AttackIQ Ready! 2.0, a managed breach and attack simulation-as-a-service that combines fully automated and on-demand adversary emulation testing to allow organizations to rapidly validate their cyber defense. AttackIQ Ready! 2.0 introduces added customization and seamless integration with AttackIQ’s Flex service to extend testing anywhere through a simplified user experience. The combination ...
Darwinium introduces behavior identification to strengthen online transaction security
Australian digital security and fraud prevention startup Darwinium Pty. Ltd. today announced the addition of behavior identification to its security and fraud prevention solution to give companies insight and surety when validating online transactions and user journeys. The features for verifying the authenticity of an online user and the intent behind their digital interactions is provided by ...