 NEWS
NEWS
 NEWS
NEWS
 NEWS
NEWS
![]() What do CryptoLocker and Healthcare.gov have in common? Well, they’re both big, they are both affecting a lot of people, and there’s a lot of nasty code in both of them. Not to start a trend here, but perhaps at some point starting now every technology disaster and threat will be likened to the steaming lump that is Healthcare.gov. A hilariously bad website, hilariously expensive, poorly managed throughout and a complete rebuild underway that has no chance of delivering on time. One day we’ll look back and laugh, except no, not really. But this article is about CryptoLocker and the numerous continued reports of how this particularly nasty piece of malware is spreading.
What do CryptoLocker and Healthcare.gov have in common? Well, they’re both big, they are both affecting a lot of people, and there’s a lot of nasty code in both of them. Not to start a trend here, but perhaps at some point starting now every technology disaster and threat will be likened to the steaming lump that is Healthcare.gov. A hilariously bad website, hilariously expensive, poorly managed throughout and a complete rebuild underway that has no chance of delivering on time. One day we’ll look back and laugh, except no, not really. But this article is about CryptoLocker and the numerous continued reports of how this particularly nasty piece of malware is spreading.
![]() Now, quite a bit has been done in preliminary research on this thing by various outfits in the security community. Bottom line – it’s ugly and it will be tough to shut down. Tens of thousands of new infections are turning up each week – a torrid pace that is picking up fast. This malware takes a solid hold of victim computers and spreads quickly.
Now, quite a bit has been done in preliminary research on this thing by various outfits in the security community. Bottom line – it’s ugly and it will be tough to shut down. Tens of thousands of new infections are turning up each week – a torrid pace that is picking up fast. This malware takes a solid hold of victim computers and spreads quickly.
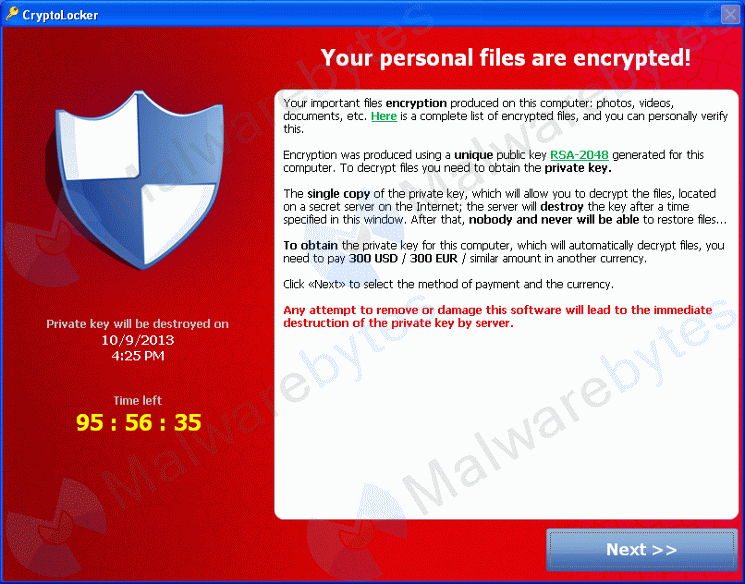
CryptoLocker first hit the scene as a Trojan, propagated through mass phony emails. It then encrypts the files on a user’s computer and all the files that are in mapped drives. You then get a message demanding you pay with a Bitcoin or MoneyPak payment within three days. Officially it’s the class of malware known as ransomware – basically it locks up computers and urges the user to pay to remove malware, but of course that never really happens. It’s been a couple of months since this first really emerged, and the financial motive behind the malware is pretty obvious in this case.
![]() Here’s where it gets crazy. At one time, those who caved and paid the two Bitcoins would get the key to un-encrypt their files. The threat was something they actually made good on because if you missed the 72 hour window – the key was gone *POOF*. Ever since November 1st however, things have changed, well the price has changed. After the 72 hour window, the key doesn’t get thrown out but the price goes up to 10 Bitcoins. Just translate that into dollars based on the day’s value for perspective on that. The point is that the threat is actively evolving, very sophisticated and will be very hard to stop. Thus far the rate of infection indicates that defense measures haven’t come up to speed quickly enough and there is a very real demonstrated likelihood that whatever measures are deployed to largely prevent infections will just be developed around by the parties running the CryptoLocker operation.
Here’s where it gets crazy. At one time, those who caved and paid the two Bitcoins would get the key to un-encrypt their files. The threat was something they actually made good on because if you missed the 72 hour window – the key was gone *POOF*. Ever since November 1st however, things have changed, well the price has changed. After the 72 hour window, the key doesn’t get thrown out but the price goes up to 10 Bitcoins. Just translate that into dollars based on the day’s value for perspective on that. The point is that the threat is actively evolving, very sophisticated and will be very hard to stop. Thus far the rate of infection indicates that defense measures haven’t come up to speed quickly enough and there is a very real demonstrated likelihood that whatever measures are deployed to largely prevent infections will just be developed around by the parties running the CryptoLocker operation.
Just today the news emerged that a Swansea, Massachusetts police department was infected by this malware and they admitted to paying the ransom to get the key.
The department paid $750 for two Bitcoins — an online currency — to decrypt several images and word documents in its computer system, Swansea Police Lt. Gregory Ryan said.
“It was an education for (those who) had to deal with it,” Ryan said, adding that the virus did not affect the software program that the police department uses for police reports and booking photos.
![]() The Swansea police department encountered the reality that many already have – once infected, there is no way to retrieve the locked files until the ransom is paid. MalwareBytes has put out an advisory on how to use their software to remove the infection, but confirms that there is no method to reclaim the actual files. Nasty. If you find a system that gets infected – TAKE IT OFFLINE IMMEDIATELY. Minimize the damage and then start to consider what may have been on that system.
The Swansea police department encountered the reality that many already have – once infected, there is no way to retrieve the locked files until the ransom is paid. MalwareBytes has put out an advisory on how to use their software to remove the infection, but confirms that there is no method to reclaim the actual files. Nasty. If you find a system that gets infected – TAKE IT OFFLINE IMMEDIATELY. Minimize the damage and then start to consider what may have been on that system.
The perpetrators that have unleashed this voracious infection on the internet have managed to frustrate authorities through a number of interesting methods. First off, the malware system features the now-familiar command-and-control server component that puts the communications and control of the infected systems onto specialized internet servers. Research has emerged that indicates the operation is rather nimble, where the command-and-control servers exist for maybe one week at a time. This kind of fluid nature will make it very difficult for any kind of authorities to seize the servers. There is some research that indicates the targets and the operation are US-based, based on the payment systems, and some analysis of the ongoing communications, but it is also believe to have emerged from one of the former Soviet nations. We have seen botnets shut down or impacted by the efforts of law enforcement and companies when they’ve taken the servers that control the network off the grid. It remains to be seen what the first major victory against this plight may be or when it may come, but researchers certainly realize the destructive nature of this operation and are taking the threat quite seriously.
And before anyone asks, I don’t the NSA will be decrypting people’s files for them.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.