The Internet of deadly things: IoT security almost non-existent
![]() The Internet of Things has the potential to transform our lives, but the security vulnerabilities it introduces have the potential to derail our lives, too.
The Internet of Things has the potential to transform our lives, but the security vulnerabilities it introduces have the potential to derail our lives, too.
According to a freshly baked Hewlett-Packard Co. study, a worryingly high 70 percent of Internet of Things devices, including sensors and connected infrastructure, possess vulnerabilities that hackers could easily exploit.
HP’s data comes by way of its Fortify division, which looked at ten of the most popular IoT devices, including TVs, webcams, door locks, alarms, garage openers, thermostats, power outlets and sprinklers. It put these devices through rigorous analysis to identify their weak spots. It found an average of 25 vulnerabilities per device. One of the biggest issues was a laissez-faire attitude toward privacy. HP said that eight out of 10 gizmos it tested raised concerns about the collection of private data, like names, emails, home addresses, dates of birth, credit card details and health data.
The Internet of Gaping Holes
That kind of data collection itself probably wouldn’t worry too many people, but a shocking 70 percent of devices didn’t use any kind of encryption at all, while half of the devices’ mobile apps were also guilty of sending unencrypted communications to the cloud and Web. Moreover, 80% of the devices failed to require a strong password – which makes them vulnerable to brute force attacks – and six in ten had “insecure web interfaces”, according to HP.
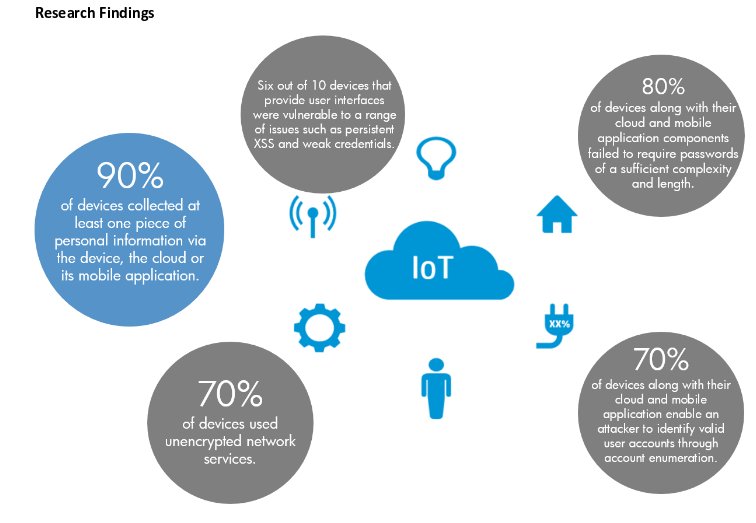 Graphic via HP Fortify
Graphic via HP Fortify
IoT security concerns have been raised before, but competition demands that hardware manufacturers get their products to market quickly – a fact that tends to make security an afterthought. And the problem isn’t just for consumers. Research firm Forrester predicts that “By 2020, wearable technology will be common within many organizations,” meaning that a single gadget inside the firewall could potentially blow open a hole in network security.
“Using vulnerabilities, attackers can do two main things: get closer to your data for malicious purposes or use your compromised systems as a launching point for other attacks,” said Daniel Miessler, Practice Principal for Fortify on Demand at HP Fortify. “Once attackers have access to your network, they gain access to a host of your company’s private data and information and/or use that foothold to attack other locations. Both are bad for the victim.”
Security technology is lagging behind device adoption, which means that organizations that allow employees to use IoT devices largely take security into their own hands.
“The main two takeaways we’d like people to come away with from this study are that IoT security is not one-dimensional,” said Miessler. “You need to look at all the surface areas discussed in the report, while corporations need to be looking at how their ICS (incident command system) and SCADA (supervisory control and data acquisition) systems fare when looked at under a similar light.”
Main photo credit: waitscm via photopin cc
A message from John Furrier, co-founder of SiliconANGLE:
Your vote of support is important to us and it helps us keep the content FREE.
One click below supports our mission to provide free, deep, and relevant content.
Join our community on YouTube
Join the community that includes more than 15,000 #CubeAlumni experts, including Amazon.com CEO Andy Jassy, Dell Technologies founder and CEO Michael Dell, Intel CEO Pat Gelsinger, and many more luminaries and experts.
THANK YOU









