 NEWS
NEWS
 NEWS
NEWS
 NEWS
NEWS
But with that promise comes great peril as well. Connected devices to the Internet, also known as Internet of Things, can be easily hacked, as we saw last week when hackers marshaled millions of devices such as webcams for a global Distributed Denial of Service attack. This caused most of the Internet to go down, including popular sites such as Twitter, SoundCloud, Spotify, Netflix, Reddit and PayPal.
In short, Internet of Things devices are allowing anyone to create new attack vectors with zero accountability for companies to make the devices secure. Houston, we have a problem!
New IoT devices are showing a huge weakness in IT departments’ networks and software. This is scaring the heck out of corporate information technology departments and new security practices take time, money and qualified people to manage.
Big companies are stepping up. This week at IBM Corp.’s World of Watson show, the company is putting its weight behind big data to drive into the IoT marketplace. So are lots of competitors such as Amazon Web Services, Microsoft Azure, Oracle Corp. and a slew of new startups.
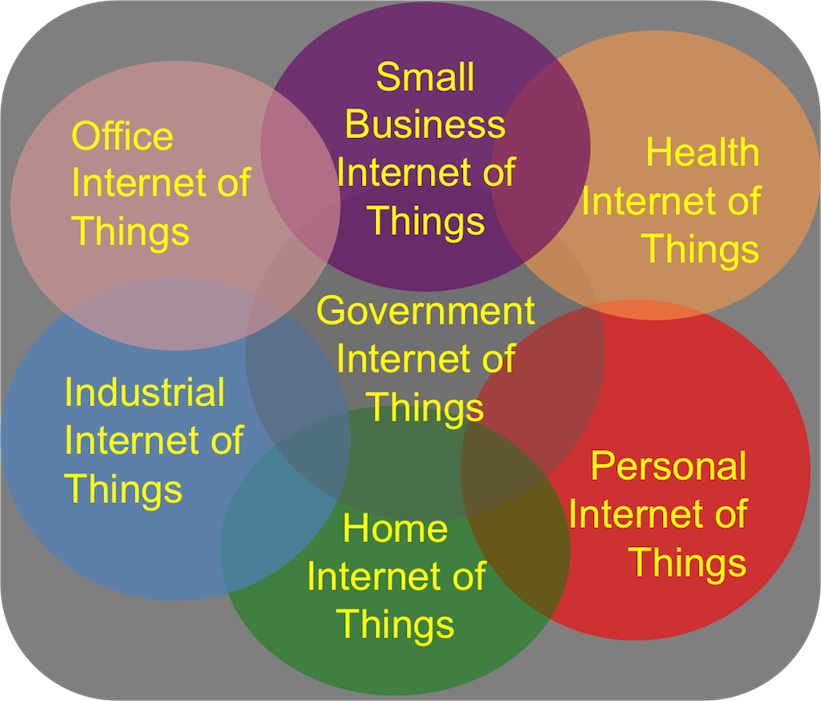
In hopes of making more sense of the IoT landscape, Wikibon Research published a recent reporting breaking down the key segments and how to deal with IoT data.
Personal IoT
Smart phones, smart cars, entertainment, location, travel, wearables, etc.
Home IoT
Smart meters, security and access control, smart appliances, health & safety, etc.
Government IoT
Federal, state & local government: criminal justice, internal security, traffic management, emergency response, etc.
Health IoT
Smart equipment, home health, electronic medical records, provider and payor applications, etc.
Small Business IoT
Asset management, smart retail, customer management, inventory, security, health & safety, etc.
Office IoT
Building management: security and access control, equipment management, utilities management, maintenance, etc.
Industrial IoT
Plant operations, equipment maintenance (predictive and preventive), vehicle and fleet management (aircraft, trucks, shipping, trains, etc.), warehouse operations and inventory management, site health & safety, security and access control, etc.
It will be very difficult to justify big data projects as security concerns will put efforts on hold. Another issue is that if all the data is extracted and sent to the cloud, the cost and elapsed time for data transmission is likely to be prohibitive, and the results delayed and reduced in value.
Some of the smartest engineers working on IoT are using distributed data analytics at big data centers, and extracting small amounts of data for further analysis in the cloud. Connected devices and industrial projects can also turn on specific filters to save additional data at the edge of the network for processing and onward transmission of results.
What about security in IoT?
What can be done is not easy, but according to Wikibon, companies can rethink how to deal with IoT. Connecting systems to share information around big data is something Splunk is doing. Security software that has native big data capabilities, native in devices that send notifications for any vulnerability activity. Cloud-based software to manage scaling agile software development practices as hackers tend to use holes in new software to find entry points from IoT devices. Even last week, Dave Vellante reported on theCUBE that IoT devices are shipping with default passwords increase the scale of potential hacks.
Digital business goals require greater cooperation and coordination of modern technologies and organizations. To extract the maximum value from big data it will need to be streamed, reduced and processed locally. IoT projects should focus primarily on giving value to the connected business processes. Value of data can be processed and delivered to upstream parties who pay for it, subject to careful review. Big data projects will be designed with distributed big data analytics combined with hybrid cloud services.
Most importantly, companies need to find a cloud and big data partner whose products are state of the art, where security is designed into the overall plan from the start.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.