 NEWS
NEWS
 NEWS
NEWS
 NEWS
NEWS
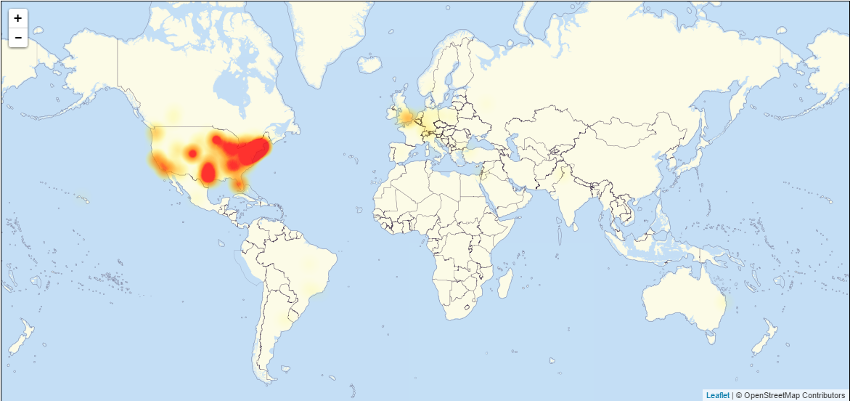
A massive distributed denial of service attack that brought down leading sites across the world on Friday is being attributed to script kiddies, or people who use existing scripts or programs, who wanted to take down the PlayStation Network, a report published Tuesday claims.
The attack, which targeted domain name server hosting provider Dynamic Network Services Inc., known as Dyn, took sites including Twitter, Amazon.com, Reddit, PayPal, Netflix, Spotify, Etsy and a range of others down twice on Oct. 21. Because of the scale of the attack, there was speculation that criminal organizations or even foreign governments might be involved.
According to analysis from security firm Flashpoint Global Partners Inc., the attack came from a group of users linked to the Hackforums community. They used the Mirai botnet, which consists of compromised consumer devices such as routers, DVR systems and web cams. The botnet in question had previously been used in the DDoS attack against the Krebs on Security blog and French internet service provider OVH.
In its post making its argument, Flashpoint drew the dots between various points of the attack, stating that they were moderately confident in their finding.
Since the attack occurred a variety of groups have been blamed for the attack. Naturally in a year where neo-McCathyism has come to the forefront of the President campaign, be it ironically now coming from the left versus the right, the Russian Government was blamed for the attack, particularly given that it brought down primarily American websites.
Over the weekend others have claimed or implied responsibility, including Wikileaks, who posted a tweet asking their supporters to stop attacking Dyn on Twitter, and a group called the “New World Hackers” who claimed responsibility on their Twitter account.
“Flashpoint assesses with medium confidence that each of these claims is dubious and likely to be false,” the company noted. “Flashpoint assesses with moderate confidence that these attacks were not financially or politically motivated. Typically, financially motivated DDoS attacks will target business competitors, online gambling sites, or Bitcoin exchanges. Despite various groups claiming responsibility for the attack, there have been no publicly available indicators of extortion — attempted or not — against Dyn DNS or any of the sites affected by the attack.”
Flashpoint said the technical and social indicators of the attack align more closely with attacks from the Hack Forums community than the other type of actors that may be involved, such as higher-tier criminal actors, hacktivists, nation-states, and terrorist groups. Those groups, it added, “very unlikely to launch an attack against a video game company.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.