 INFRA
INFRA
 INFRA
INFRA
 INFRA
INFRA
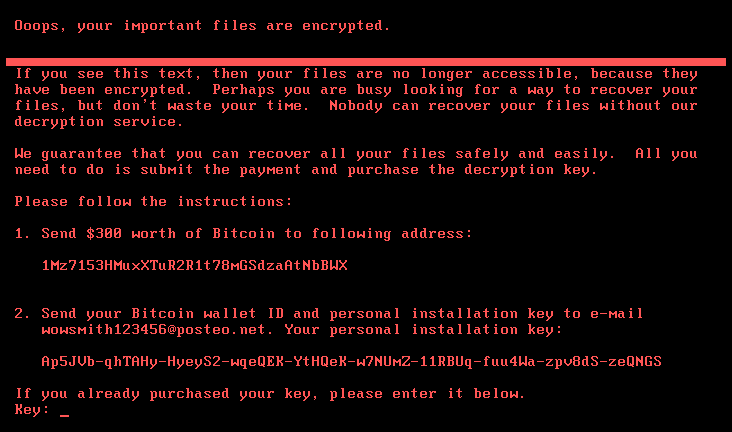
Police in Ukraine have raided a company alleged to be ground zero in the distribution of the recent NotPetya malware cyberattack.
Local authorities early Wednesday local time said they seized computers from a company called Intellect Service that sells accounting software under the names of IS-pro and M.E.Doc. It’s alleged to be the main point of distribution for NotPetya, a cyberattack that was first thought to be ransomware but turned out to be a “wiper,” or malicious code that pretended to be ransomware but instead permanently wipes files from a computer.
According to the Associated Press, the company’s computers were seized to “immediately stop the uncontrolled proliferation” of malware that a Ukrainian Cyberpolice spokesperson suggested had been sent or was preparing to be sent as an update to NotPetya. The “swift action had prevented any further damage,” the spokesman said. The Ukrainian Cyberpolice added that the company’s management and staff fully assisted in the investigation and that the seized equipment will be “sent for detailed analysis.”
The Ukranian Cyberpolice were quick to blame Russia for the attack, claiming that the company was working with Russia to undermine Ukrainian sovereignty. “We have issues with the company’s leadership, because they knew there was a virus in their software but didn’t do anything … If this is confirmed, we will bring charges,” Col. Serhiy Demedyuk, the head of Ukraine’s national cyber police told Reuters.
Whether Russian or not, NotPetya again highlighted vulnerabilities in computer networks across the enterprise world. “Attacks like NotPetya and WannaCry are making organizations face the realities of today’s cyberthreat landscape,” Brad Taylor, chief executive officer at security firm Proficio Inc., told SiliconANGLE. “Hackers are constantly seeking and exploiting vulnerabilities across all enterprise resources; your people, processes and technology are all targets to advanced cybercriminals.”
Taylor was not all negative, adding that “accurate monitoring can allow your organization to proactively identify the early stages of an attack and more efficiently halt suspicious or high-risk behavior.” Most breaches only take 30 minutes to compromise an entire system, he said. Although prevention is paramount, “attackers will continue to find the cracks, and stopping attacks earlier in the ‘kill chain’ can minimize the impact of a hack once a network is infected.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.