 INFRA
INFRA
 INFRA
INFRA
 INFRA
INFRA
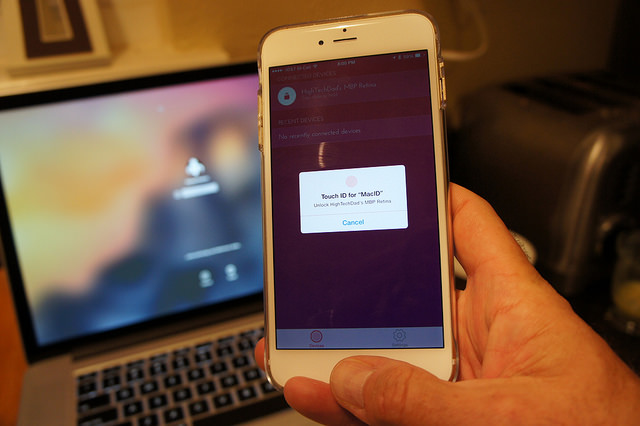
Israeli security company Cellebrite, a major U.S. government contractor perhaps best known as the company that assisted authorities to crack the iPhone used by the San Bernardino massacre shooter, is now claiming to have found a way to unlock nearly every iPhone on the market.
The claim suggests that iOS 11 isn’t as secure as Apple Inc. claims it to be. According to Forbes, the firm hasn’t made any major public announcement about its new iOS capabilities, but two sources claimed that the iPhone hacking breakthrough, involving undisclosed techniques to get into iOS 11, occurred recently and the company is advertising the fact to law enforcement and private forensics folks worldwide.
Adocument currently sitting on Cellbrite’s own server, dated from January, makes the following claims, meaning that the ability to hack iOS 11 may not be such a big secret after all:
Devices supported for Advanced Unlocking and Extraction Services include:
Apple iOS devices and operating systems, including iPhone, iPad, iPad mini, iPad Pro and iPod touch, running iOS 5 to iOS 11.
Google Android devices, including Samsung Galaxy and Galaxy Note devices; and other popular devices from Alcatel, Google Nexus, HTC, Huawei, LG, Motorola, ZTE, and more.
“This is certain to elevate the debate between technology firms and law enforcement about data privacy and access,” Ben Johnson, co-founder and chief technology officer of Obsidian Security Inc., told SiliconANGLE. But in the current climate, he said, nothing is really private.
“If you have information on a device, people who are determined to get it — whether that’s government entities or hackers — probably can,” Johnson said. “While that is concerning for consumers, we should expect that companies like Apple will only use these tools to their advantage to patch any vulnerabilities that they may exploit.”
Discussing the broader ramifications, Rod Soto, director of security research at JASK, noted that keeping new exploits secret in the name of security or for law enforcement is dangerous.
“In addition to this potentially impacting civil rights and due process, it also relies heavily on the ability of Cellebrite (and similar firms) to keep the code out of the hands of malicious actors,” Soto said. “It’s difficult to do this, as evidenced by the leaks of NSA exploitation code. Once bad actors gain access to tools like these, they can move on aggressive mass exploitations that have the potential to cause extensive losses and, in some cases, put the general population’s well-being at risk.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.