 INFRA
INFRA
 INFRA
INFRA
 INFRA
INFRA
Security researchers at Cyberbit Ltd. have uncovered a new way that hackers can hijack Windows installations using a vulnerability in Microsoft Corp.’s Component Object Model.
The Microsoft COM is a platform-independent, distributed, object-oriented system for creating binary software components that can interact with each other. They’re the foundation technology for Microsoft’s OLE that allows embedding and linking to documents and other objects and ActiveX, a software framework for content downloaded from a network, particularly from the web.
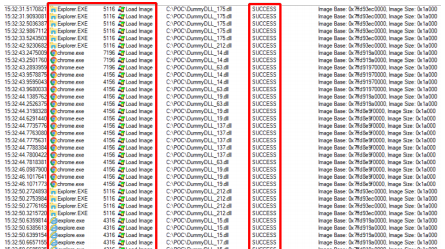
The technique discovered by Cyberbit involves code injection using Phantom COM objects that are detected by Windows as being legitimate because they use the object ID of a trusted application. In bypassing existing security methods, hackers can inject a malicious file that may result in the file being loaded and executed by the operating system.
A proof-of-concept detailed by Cyberbit shows that the method is fairly simple to apply. “We mapped the registry keys which failed to find and load a file and attempted to use these keys to load our own dummy DLL,” the researchers explained. “As we expected, we were able to do this with numerous keys and successfully loaded and ran our DLL within the context of legitimate applications such as explorer.exe svchost and powershell.”
Although this is the first time the technique has been detailed, the researchers discovered several samples that use these keys in the wild, but not as many as they would have expected “given the simplicity of using these techniques and the lack of security awareness for this risk.”
“Our little experiment was a troubling success,” they concluded. “We discovered that hundreds of registry keys are vulnerable to COM hijacking and Phantom COM Objects loading. This process is very easy for attackers to implement and does not require sophisticated or code injection which is more visible to detection platforms. It is more dangerous because it run using legitimate user privileges, often does not require reboot and may not have any visible side effects on the user.”
The researchers recommend that organizations verify that their endpoint security vendors mitigate the risk by monitoring COM search order hijacking and Phantom COM objects loading and that endpoint security vendors increase their awareness and support against the technique.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.