 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
The ransomware used to cripple the City of Baltimore last month did not include code from the U.S. National Security Agency’s leaked EternalBlue hacking exploits, according to a security analyst.
The finding comes from Joe Stewart, a malware analyst now consulting with security firm Armor Defense Inc. Krebs on Security reported today that he was unable to find any evidence of EternalBlue code in the Robbinhood ransomware used in the attack.
“We took a look at it and found a pretty vanilla ransomware binary,” Stewart said. “It doesn’t even have any means of spreading across networks on its own.” Stewart did note that it is possible that EternalBlue could have been used to propagate the ransomware but it’s “not terribly likely.”
Stewart’s analysis contradicts a report from The New York Times May 26 which claimed that the EternalBlue exploits were used in the attack targeting Baltimore. That report referenced the finding to Thomas Rid, a cybersecurity expert at Johns Hopkins University.
Rid has yet to comment publicly on the new report claiming that EternalBlue was not involved in the attack, but he’s currently writing a book called “Active Measures: The Secret History of Disinformation and Political Warfare.”
The NSA has never confirmed the existence of EternalBlue but denied any involvement in the attack targeting Baltimore, via a Maryland congressman May 31.
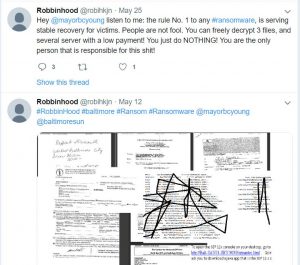 In another twist to the story, Eric Sifford, a security researcher at Armor published a separate report that claimed the entity behind the ransomware attack on Baltimore was seemingly taunting the city’s mayor on Twitter.
In another twist to the story, Eric Sifford, a security researcher at Armor published a separate report that claimed the entity behind the ransomware attack on Baltimore was seemingly taunting the city’s mayor on Twitter.
A Twitter account going by the name of @robinkjn, which has since been suspended, sent out a series of tweets to Bernard C. Jack Young that included documents that may have been stolen in the attack.
“One of the documents indicates that it has been scanned/copied on May 4, 2019 and pertains to a June 2018 court case where the mayor and City Council of Baltimore City are being sued by an individual,” Sifford wrote. “The other document appears to have been copied/scanned on April 23, 2019 and pertains to a worker’s comp medical file which went to the City of Baltimore.”
Sifford cautioned that the person or persons behind the account may have been a malicious prankster, although the evidence would indicate otherwise.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.