 CLOUD
CLOUD
 CLOUD
CLOUD
 CLOUD
CLOUD
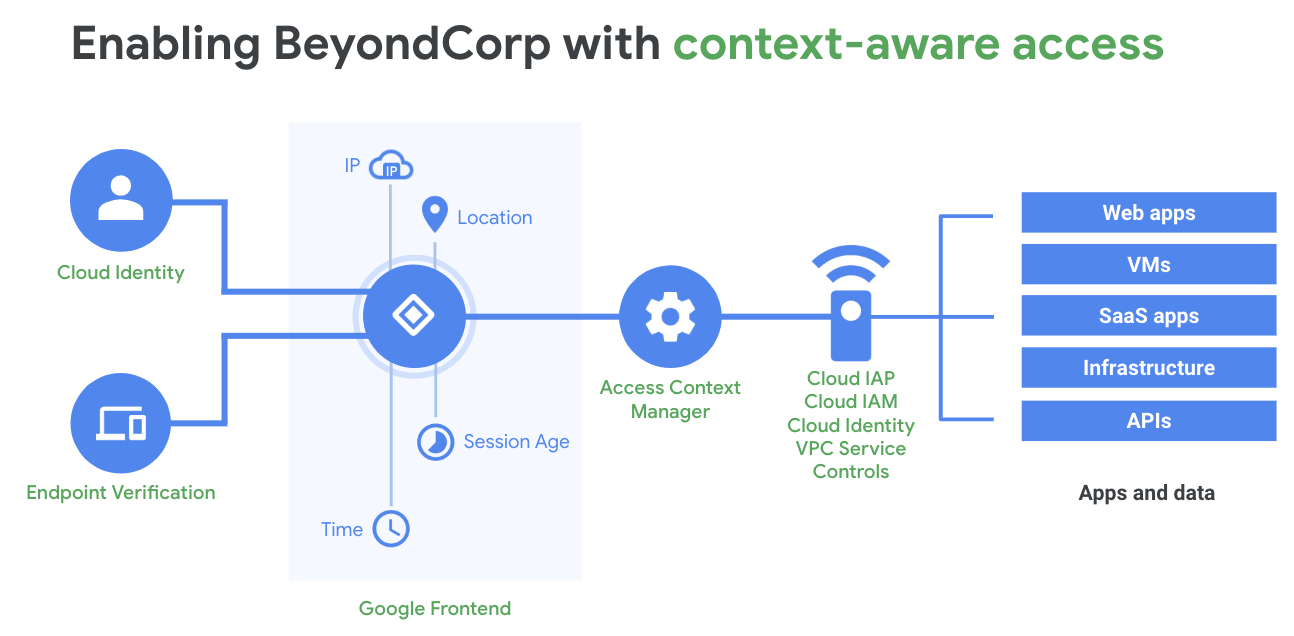
Google LLC is making new context-aware access capabilities in its cloud-based Identity-Aware Proxy service generally available today as it tries to encourage wider adoption of its BeyondCorp, or “zero-trust,” security model among its enterprise customers.
The zero-trust security model is a framework that involves shifting access controls from the perimeter to individual devices and users, allowing employees to work securely from any location without the need for a traditional virtual private network.
Google created the model for its own use back in 2010 after it fell victim to Chinese hackers who gained access to its network and stole intellectual property. Those attacks prompted Google to move away from the traditional access control approach to its security, which rely on outdated concepts such as virtual private networks.
With zero-trust, access control is no longer based on whether users are requesting that access from inside or outside of the corporate network. Instead, the model assumes that users requesting access from inside the network are just as untrustworthy as those seeking remote access. As a result, access requests are instead granted based on details about the particular users, their jobs and the security status of the device they’re using.
Google is so convinced of the merits of the zero-trust model that it has been trying to encourage enterprises to adopt it for several years already. As part of this effort, it recently enhanced the context-aware access capabilities of its IAP service to help organizations protect against unauthorized access to their virtual machines. Announced as a preview in January, the capability is now being made generally available, Google Cloud product manager Christiaan Brand said in a blog post today.
The new capability means that enterprise admins can for example, provide access to certain VMs for groups of users, based on their identities and the context of that request, such as the security status of the device being used, or the user’s location. The main benefit is convenience, as this can be done without needing to provide the VMs with public IP addresses, and without having to set up bastion hosts, which are special nodes that are set up to filter incoming traffic and prevent anything malicious from entering the network.
“Context-aware access allows you to define and enforce granular access policies for apps and infrastructure based on a user’s identity and the context of their request,” Brand said. “This can help strengthen your organization’s security posture while giving users an easier way to access apps or infrastructure resources without using a VPN client, from virtually any device, anywhere.”
The new capabilities are accessible via the Google Cloud Platform admin control panel.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.