 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
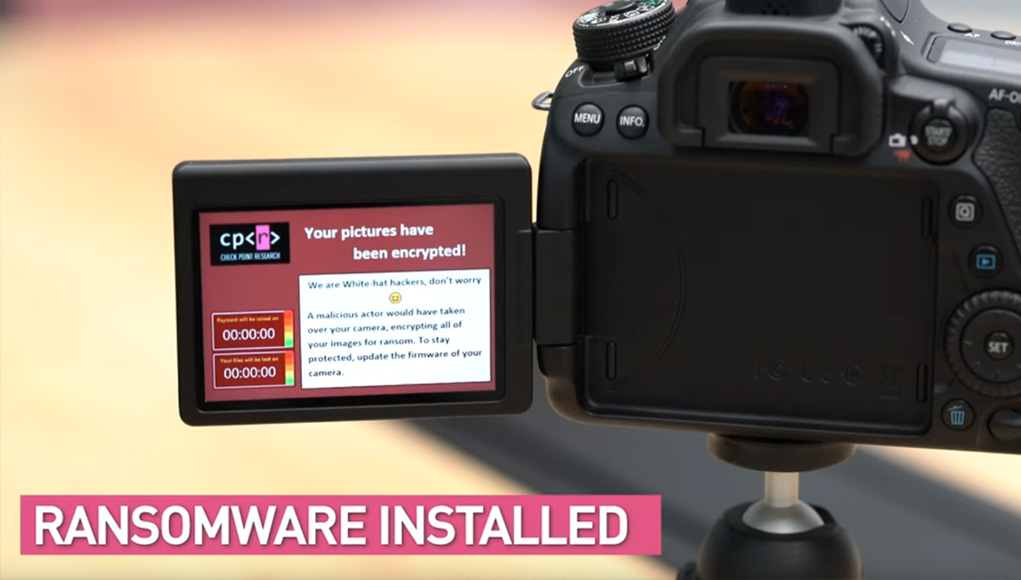
Ransomware has long been a bane of computer networks, but a new report has demonstrated how ransomware can be used to target digital single-lens reflex cameras.
Demonstrated by a security researcher from Check Point Software Technologies Ltd., the technique involves exploiting a vulnerability in the picture transfer protocol used in a Canon EOS 80D digital camera.
PTP is a protocol used to transfer images from digital camera to computers with support for both USB cables and Wi-Fi connections. The exploitable vulnerability stems from the fact that PTP is an unauthenticated protocol that can support multiple streams of data, including malicious commands.
In a demonstration video, Check Point’s Eyal Itkin showed how it can be done in under 60 seconds. Itkin turns the camera on, takes some pictures then uses a laptop to connect to the WiFi access point on the camera itself. He then uploads the ransomware via the connection with the camera both encrypting the photos and showing a ransom message.
“Our research shows how an attacker in close proximity (WiFi), or an attacker who already hijacked our PC (USB), can also propagate to and infect our beloved cameras with malware,” Itkin wrote. “Imagine how would you respond if attackers inject ransomware into both your computer and the camera, causing them to hold all of your pictures hostage unless you pay ransom.”
Check Point did advise Canon of its findings well in advance — March 31 — and Canon has now published a security advisory and patch. The patch, though, depends on users updating their camera software, not something many users would ever think of doing.
Although it was demonstrated using a Canon EOS 80D, the vulnerability is on other cameras made by the company, and it likely is not exclusive to Canon.
“Although the tested implementation contains many proprietary commands, the protocol is standardized, and is embedded in other cameras,” Itkin noted. “Based on our results, we believe that similar vulnerabilities can be found in the PTP implementations of other vendors as well.”
THANK YOU