 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
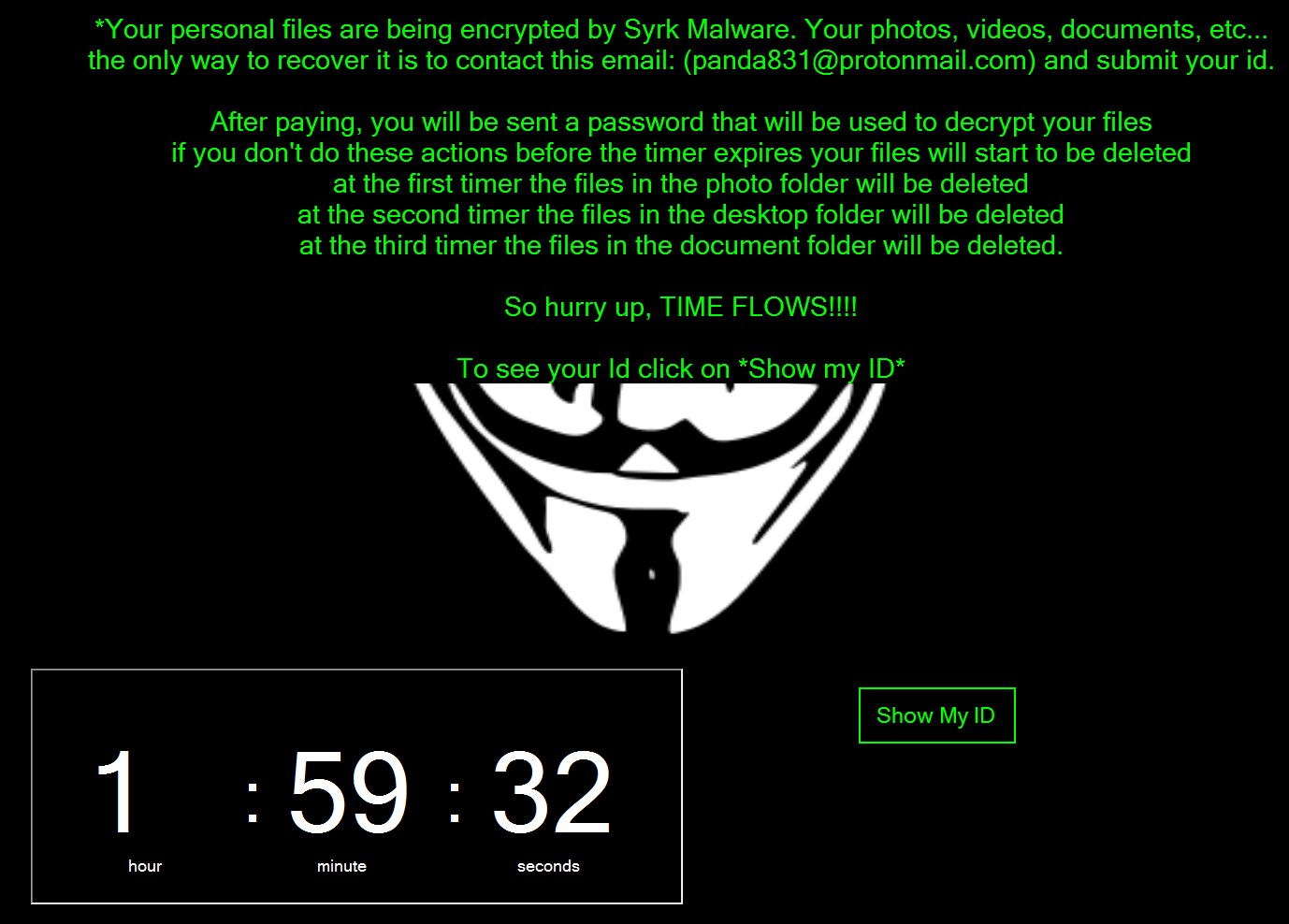
Players of Fortnite, the world’s most popular computer game, are being targeted by ransomware pretending to be a hack that allows players to aim more accurately when playing the game.
Detailed Tuesday by security researchers at Cyren Ltd., the Syrk ransomware was found to be masquerading as an “aimbot” that in addition to improving a player’s aim also claimed to assist players in identifying the location of others players in the game.
The code for Syrk uses the code of Hidden-Cry, an open-source form of ransomware that is widely available and was available on GitHub for a time. Like various forms of ransomware before it, the code encrypts files and demands a ransom payments with the addition of threats that files will be deleted every two hours until such time that the ransom payment is made.
The good news is that thanks to its use of open-source code, the researchers found that it’s possible to decrypt target files and recover any that have been deleted using a Hidden-Cry decryption tool.
With an estim ated 250 million users worldwide, Fortnite players have been targeted by other scams previously. That ransomware has been thrown into the mix shouldn’t come as a great surprise.
ated 250 million users worldwide, Fortnite players have been targeted by other scams previously. That ransomware has been thrown into the mix shouldn’t come as a great surprise.
“Combining game malware with ransomware was inevitable,” Chris Morales, head of security analytics at cybersecurity firm Vectra AI Inc., told SiliconANGLE. “Social engineering through online video games has been going on for some time. It is a large audience to target and an industry that is known to look for shortcuts.'”
The problem, he added, is that “Malware posing as a hack tool is novel as it will not be validated by any app store and bypasses the normal security controls. This makes encrypting files using a game hack highly opportunistic and easy to execute. This ransomware is effectively cheating the cheater.”
Alex Guirakhoo, strategic intelligence analyst at digital risk protection firm Digital Shadows Ltd., noted that the video game industry and gamers in general are lucrative targets for cybercriminals.
“A lot of this builds on the wide media attention that popular games receive on social media and sites such as Twitch or YouTube,” he said. “The more attention a game gets because of a new release or update, the more likely it is that a cybercriminal will be able to successfully distribute malware.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.