 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
As computing power continues to grow at the beginning of the third decade of the 21st century, it allows hackers and other bad actors to reach new records when it comes to cyberattacks.
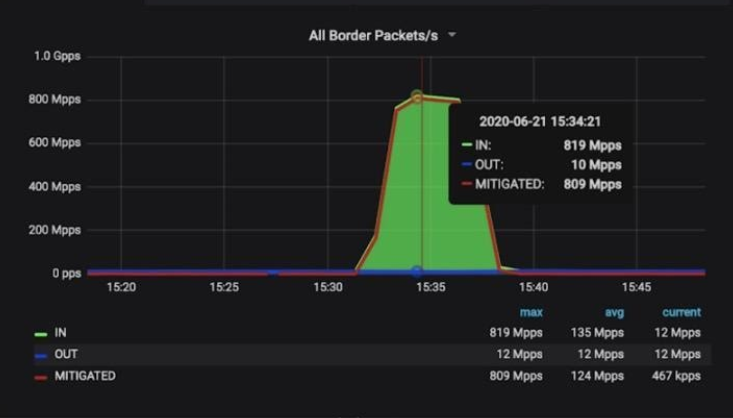
Last week, Amazon Web Services Inc. detailed how it mitigated the largest ever record distributed denial-of-service attack. Today, Akamai Technologies Inc. detailed how it mitigated the largest-ever recorded packet-per-second-based DDoS attack in history.
The attack, which targeted a European bank, occurred June 21, peaking at 809 million packets per second. When measuring DDoS attacks, there are several ways to describe them and they’re generally measured in bits per second, per the AWS example. PPS attacks — also known as Network Protocol DDoS attacks — differ in that they specifically target TCP/IP networks and are measured in packets per second, differing from a more typical volumetric DDoS attack.
“PPS-focused attacks are largely designed to overwhelm network gear and/or applications in the customer’s data center or cloud environment,” Akamai explained. “Both are volumetric but PPS attacks exhaust the resources of the gear, rather than the capability of the circuits — and these are much less common than BPS attacks.”
In this case, the PPS DDoS attack was optimized to overwhelm DDoS mitigation systems via high PPS load. The packets being sent included a massive variance in source IP address, suggesting that the attack was highly distributed in nature. Akamai notes that they saw upwards of 600 times the number of source IPs per minute than they would normally observe.
Notably, the PPS record aside, Akami also found that the vast majority of attack traffic was sourced from IPs that were never recorded in attacks prior to 2020, suggesting that the attack may have involved a previously unknown botnet.
“Successfully mitigating these large attacks requires planning and expert resources,” the Akamai report concluded. “The process starts by understanding a given customer’s traffic in depth, in order to identify normal or baseline traffic patterns and volumes and configure proactive mitigation controls. The goal is to ensure that malicious traffic can be detected and mitigated successfully, without impacting legitimate traffic.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.