 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Security vulnerabilities discovered in a smart internet-connected chastity device could allow hackers to lock users into the device.
Discovered and publicized today by security researchers at Pen Test PartnersLLP, the vulnerabilities were found in the Cellmate Chastity Cage, a device manufactured by FoShan QIUI Technology Development Co. Ltd. The device connects to a smartphone app via Bluetooth, allowing the wearer or wearer’s partner to lock or unlock access to the chastity cage.
The vulnerabilities relate to the app’s application programming interface. An insecure direct object reference vulnerability in the API leaves the door open in the app for anyone to access it without any authentication required.
Gaining access to users of the app and hence device only required an extended member code, a code that is “somewhat deterministic” and is based on the date a user signed up for the service. The researchers, however, found an even easier way to gain access with a short “friend code.”
In tests using the friend code, they were able to obtain sensitive information such as user names, phone numbers, birthdays, the exact co-ordinates where the app was opened, their longer “memberCode” value and the user’s plaintext password — that last not needed for access.
“It wouldn’t take an attacker more than a couple of days to exfiltrate the entire user database and use it for blackmail or phishing,” the researchers noted.
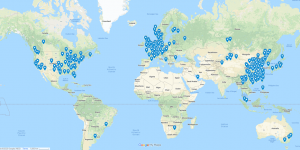 For the exercise, the researcher pulled a random set of data and were able to match the location of users across the world, raising concerns given that a number of countries “have oppressive laws that may expose users of these types of devices to unwarranted interest from law enforcement.”
For the exercise, the researcher pulled a random set of data and were able to match the location of users across the world, raising concerns given that a number of countries “have oppressive laws that may expose users of these types of devices to unwarranted interest from law enforcement.”
Gaining access to member data is one thing, but where the story takes a twist is that the same API access vulnerabilities also enable potential hackers to overwrite permissions to a user’s device, cutting off access to the locking mechanism.
“Anyone could remotely lock all devices and prevent users from releasing themselves,” the researchers wrote, adding that in the event of this happening “removal then requires an angle grinder or similar, used in close proximity to delicate and sensitive areas.”
Pen Test Partners tried to reach out to the company to address the vulnerabilities but with little success.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.