 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
A new botnet has been discovered in the wild that targets Android devices to facilitate distributed denial-of-service attacks.
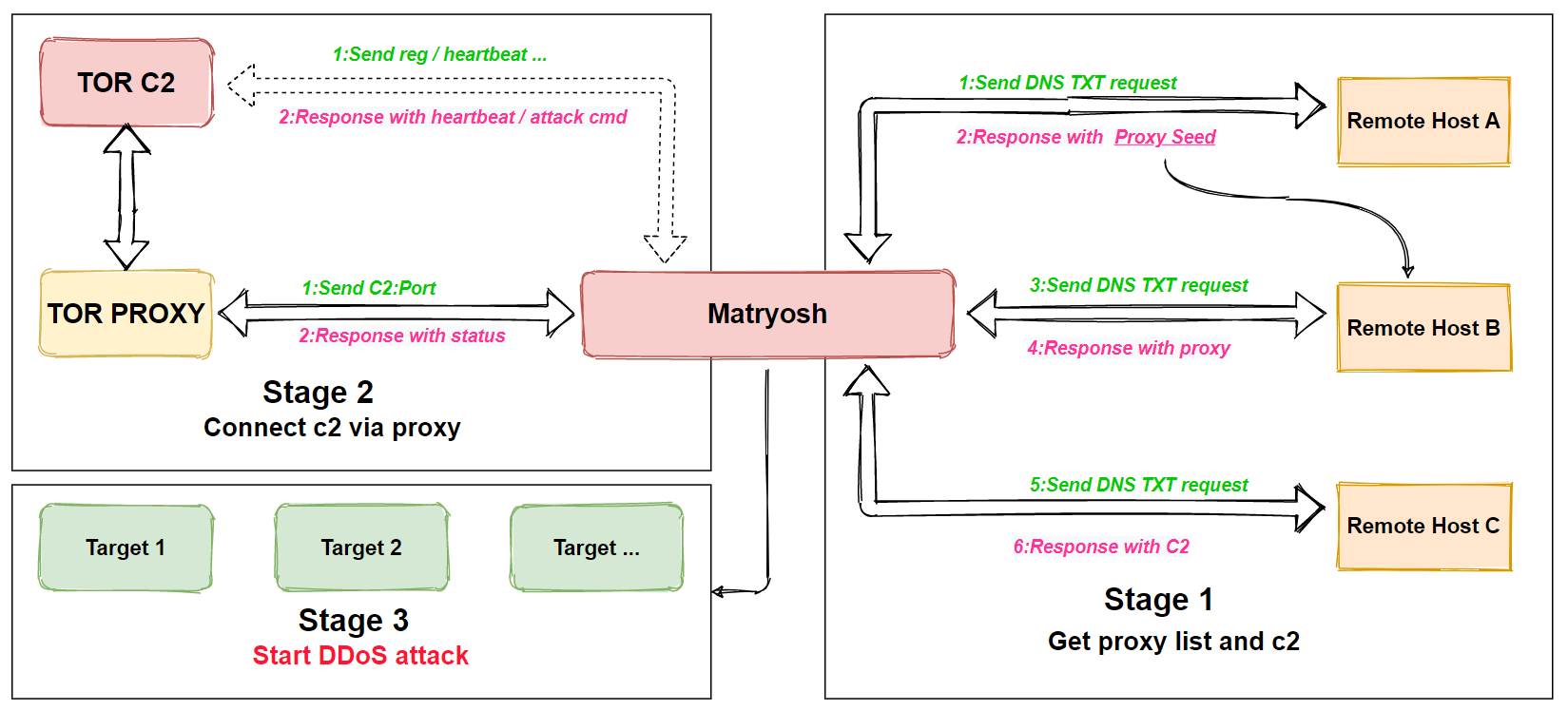
Discovered and detailed Tuesday by researchers at Qihoo 360 Netlab, the botnet was first detected on Jan. 26. It was initially believed to be an outbreak of the infamous Mirai botnet, but further investigation found that the network traffic did not match Mirai’s characteristics.
The new botnet, dubbed “Matryosh,” reuses the Mirai botnet framework with some variations. The botnet uses an encryption algorithm and a process of obtaining command-and-control using the Tor network in nested in layers, hence the botnet being named after the matryoshka Russian nesting doll.
Matryosh propagates through the Android Debug Bridge interface, a command-line tool designed to allow developers to communicate with devices directly, to execute commands on a targeted device and take control of it. ADB is typically turned off by default on most Android devices but some vendors ship devices with ADB turned on, opening the door to those behind Matryosh to connect remotely via the 5555 TCP port.
This isn’t the first time that botnet and malware developers have targeted Android devices with ADB turned on. The Satori botnet that ran between 2016 and 2018 before the mastermind behind it was arrested also targeted Android devices which had ADB turned on.
Notably, the only intent of the spread of Matryosh is for the creation of a botnet to facilitate DDoS attacks. There’s no integrated scanning features or other tools in the code that could lead to the exploitation of data on a given Android device.
“Since Android 9 and the introduction of Android Enterprise, Google has greatly improved the device management capabilities provided by mobile device management providers to limit against these types of attacks,” Burak Agca, engineer at mobile security solutions firm Lookout Inc., told SiliconANGLE. “Mobile threat defense plugs the gap where there is a requirement for users to have access to system-level features and options.”
Today, he said, administrators can block the use of ADB on corporately managed devices but not across unmanaged estates where bring your own device policies exist. “Without mobile threat defense software installed and running on personally enabled devices, corporate IT lacks visibility as to whether this feature has been enabled and a method by which to warn users and protect access to data,” Agca said. “Without mobile threat defense software installed and running, there is no way to detect if malicious payloads have been pushed to the device.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.