 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
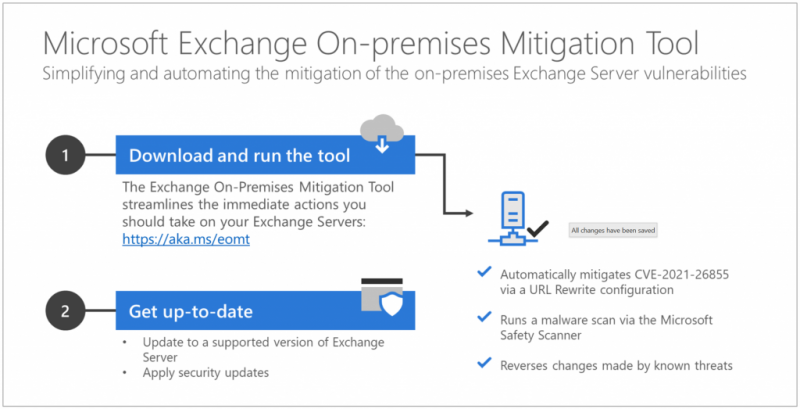
Microsoft Corp. today released a one-click Microsoft Exchange On-Premises Mitigation Tool designed to help customers apply critical security updates related to a serious vulnerability first disclosed earlier this month.
The EOMT has been created particularly to help customers that don’t have dedicated security or information technology teams to apply the relevant security updates, but it’s not limited to those customers. The tool, tested across Exchange Server 2013, 2016 and 2019, is described as an “interim mitigation for customers who are unfamiliar with the patch/update process or who have not yet applied the on-premises Exchange security update.”
Those who download the tool, which includes the latest Microsoft Safety Scanner, will automatically mitigate the vulnerability named CVE-2021-26855 on any Exchange server on which it is deployed. “This tool is not a replacement for the Exchange security update but is the fastest and easiest way to mitigate the highest risks to internet-connected, on-premises Exchange Servers prior to patching,” Microsoft explained.
The release of a tool by Microsoft comes as the attacks on Exchange services, believed to be undertaken by Chinese state-sponsored actors, continue to increase. A report on March 8 stated that the attack was larger than originally believed. An estimated 30,000 U.S. organizations were targeted, though not all of those attacks were necessarily successful.
The size of the attack also prompted the establishment of a new multi-agency “Unified Coordination Group” task force which includes U.S. Federal Bureau of Investigation and Department of Homeland Security Cybersecurity and Infrastructure Security Agency agents.
The number of attempted attacks has continued to grow. According to a report from Check Point Software Technologies Ltd., the number of attacks targeting Microsoft Exchange Server increased from 700 a day on March 11 to more than 7,200 a day on March 15. Some 17% of all exploit attempts targeted servers in the U.S., 6% targeted servers in Germany, 5% the U.K. and the Netherlands each, and 4% in Russia.
Nearly a quarter of all attempted attacks targeted Exchange servers in government and the military, followed by 15% in manufacturing, 14% in banking and financial services, 7% at software vendors and 6% in healthcare.
“This shows why organizations have to assume they’ve been breached,” Bryson Bort, chief executive officer of adversary emulation platform provider Scythe Inc., told SiliconANGLE. “However an attacker gets in, they are bound to be visible afterward. It’s especially incumbent on organizations to ensure that their vulnerability assessments service and their internal team are equipped to spot it.”
THANK YOU