 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
A newly revealed PayPal Holdings Inc. credential phishing attack is using exploited legitimate services to target victims and bypass security services provided by Google LLC Workspace.
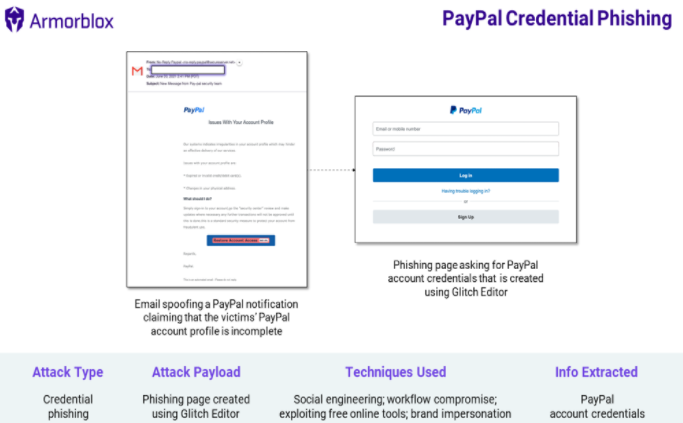
Detailed today by Bryan O’Neil, vice president of solutions engineering at email security firm Armorblox Inc., the attack exploits issues with PayPal integration with services from companies such as GoDaddy Inc. and Glitch in its phishing flow.
The phishing email attacks use a range of techniques to get past traditional email security features, including social engineering, brand impersonation, the use of security themes, replication of existing workflows and exploring legitimate infrastructure. The email sender domain is hosted on GoDaddy and the phishing page is created using Glitch Editor.
In a typical case, the email claims to come from PayPal and has a “No-Reply PayPal” as the sent name. The message subject is “New Message from Pay-pal security team.” The grammatical errors should immediately cause suspicion, but the email also claims that the victim’s PayPal profile is incomplete because of an expired credit or debit card or a change in physical address.
The domain of the email sender is securesever dot net, which is hosted by GoDaddy. After clicking “Restore Account Access,” victims are taken to a phishing page that resembles the PayPal login portal. The page asks victims for their email or mobile number and PayPal account password.
Phishing attacks are not new, but O’Neil claims that this campaign gets interesting in that the emails are getting past Google Workspace email security. Google Workspace email security is claimed to offer advanced phishing and malware protection and is designed to meet “stringent privacy and security standards based on industry best practices.”
O’Neil recommends that companies augment native email security, including additional controls with layers that take a materially different approach to threat detection. Simple personal detection is also noted as important as a simple eye test, in this case, could have found that the phishing emails were suspicious.
In addition, O’Neil also notes that using multifactor authentication and password management best practices is a must. For example, MFA on all personal and business accounts provides a layer of security against phishing and other malicious attacks. And people shouldn’t use the same password on multiple sites.
THANK YOU