 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Cybersecurity services company Group-IB Global Pvt. Ltd. has published details on previously unreported phishing operations carried out by the nation-state cyber threat actor SideWinder between June and November 2021.
SideWinder, also known as Rattlesnake, Hardcore Nationalist (HN2) and T-APT4, is a state-sponsored hacking group believed to be affiliated with the Indian government. The group has been involved in various cyber espionage campaigns targeting a range of industries, including government agencies, military organizations and energy companies.
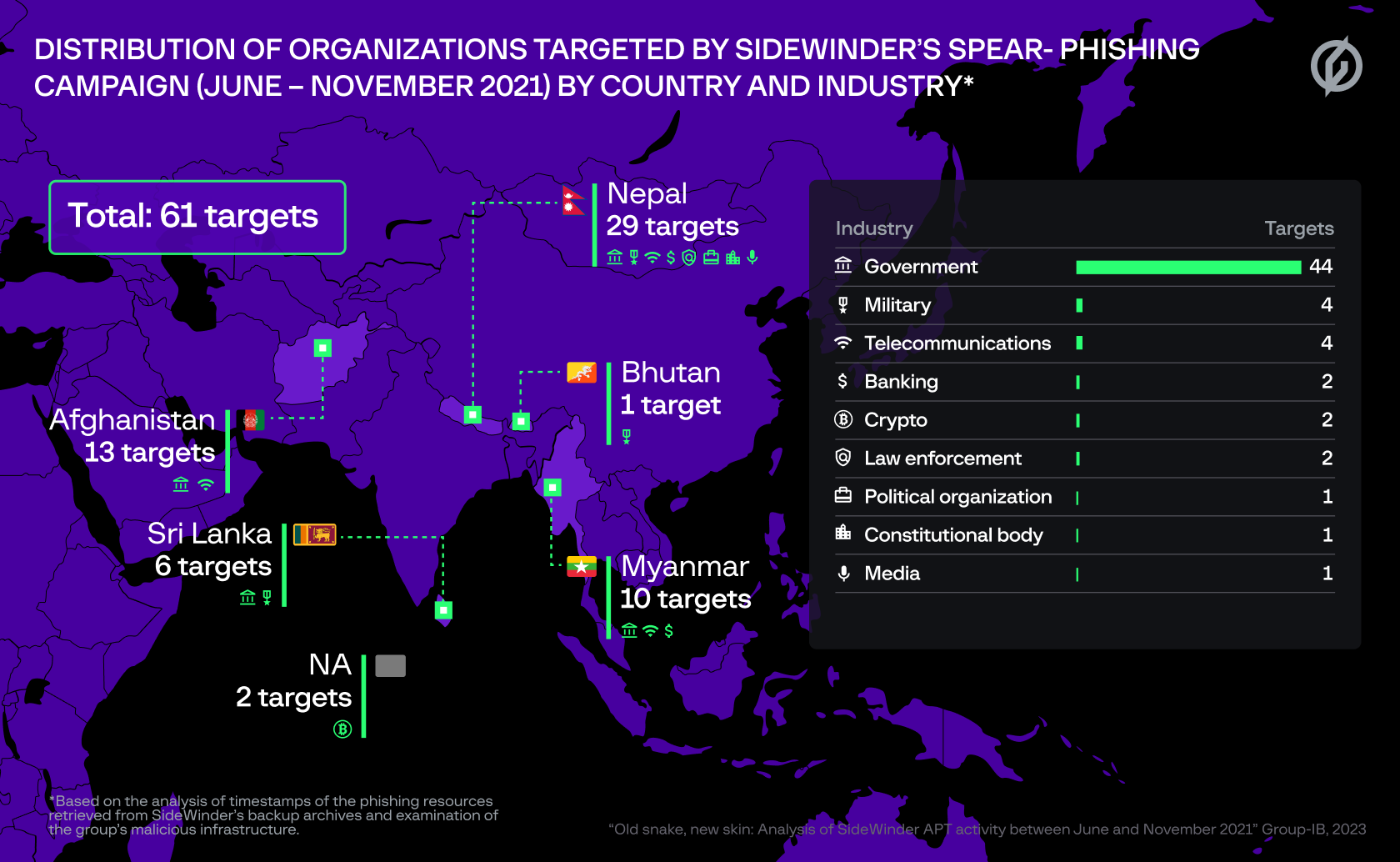
According to Group-IB, the attackers attempted to target 61 government, military, law enforcement and other organizations in Afghanistan, Bhutan, Myanmar, Nepal and Sri Lanka in 2021 (pictured). The campaign involved the hackers using Telegram to receive information from compromised networks.
In the report “Old snake, new skin: Analysis of SideWinder APT activity between June and November 2021,” Group-IB researchers confirmed links between the SideWinder, Baby Elephant, and Donot advanced persistent threat groups and described the entire arsenal of the cyberespionage group, including newly discovered tools.
In June 2022, Group-IB discovered the group’s newest custom tool, SideWinder.AntiBot.Script, which was used in previously documented phishing attacks against Pakistani organizations. SideWinder is notable for its ability to conduct hundreds of espionage operations within a short period.
During proactive threat-hunting operations, the researchers discovered backup archives on infrastructure attributed to SideWinder. One of the 2021 archives contained several phishing projects designed to target government agencies in Southeast Asia, among which were fake websites imitating the Central Bank of Myanmar.
Based on the date when the related phishing pages were edited, the Group-IB team was able to reconstruct an approximate timeline of SideWinder’s phishing operations between June and November 2021. As the phishing resources were retrieved from a backup archive by the Group-IB team, there’s a possibility that SideWinder’s attacks may have started earlier.
Further analysis allowed the Group-IB team to compile a list of the group’s 61 potential targets, which include government, military, financial, law enforcement, political, telecommunications and media organizations in Afghanistan, Bhutan, Myanmar, Nepal and Sri Lanka. It’s unknown whether any of these phishing campaigns were successful.
The researchers also discovered two phishing projects mimicking crypto companies. SideWinder’s growing interest in cryptocurrency could be linked to the recent attempts to regulate the crypto market in India.
The full report is primarily intended for analysis purposes among cybersecurity experts, but it provides interesting insight into the nefarious cyber activities of the Indian government as well. Although much of the focus on hacking and cyber threats lands on countries like Russia, China, North Korea and Iran, it’s helpful to remember that all countries — India and the U.S. included — sponsor these groups and hack other countries.
THANK YOU