 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
The National Security Agency and the Cybersecurity and Infrastructure Security Agency late last month issued an advisory memo to help improve defenses in application development software supply chains — and there’s a lot of room for improvement.
Called Defending Continuous Integration/Continuous Delivery (CI/CD) Pipelines, the joint memo describes the various deployment risks and ways attackers can leverage these pipelines, including stealing login credentials and encryption keys, and injecting malware into or taking control of source code projects. The memo relies heavily on the MITRE ATT&CK threat framework to classify these threats and provide recommended tactics and countermeasures.
“By exploiting a CI/CD environment, attackers can gain an entryway into corporate networks and access sensitive data and services,” the memo says.
The memo grew out of two well-publicized breaches: the November 2020 SolarWinds/SUNBURST attack and the December 2021 Log4Shell attack. Both had widespread reach thanks to poisoning software supply chains, and indeed last month the Securities and Exchange Commission announced it’s considering legal action against SolarWinds chief information security officer and chief financial officer because of the SUNBURST event.
But those are just the headline-grabbing events. Every day applications are compromised: Veracode Inc.’s State of Software Security report found that 76% of the 130,000 applications it tested had at least one security flaw and 24% of all apps had at least one high-severity flaw. This shows there’s plenty of opportunity — and room for improvement — to build more secure apps.
Both of these breaches happened because of the way modern software is written and, more important, revised. Apps are refined daily or even hourly with new code — that’s the implication in the “continuous” part of the nomenclature — and that makes it more of a challenge for security tools to identify and fix any coding errors quickly. It means old, more manual error-checking methods are doomed to fall behind and let vulnerabilities slip through.
The NSA/CISA document is designed for managers who aren’t information technology professionals and provides a lot of background on development pipelines, how they’re constructed and the tools used to detect potential malware compromises. They describe three common threat scenarios:
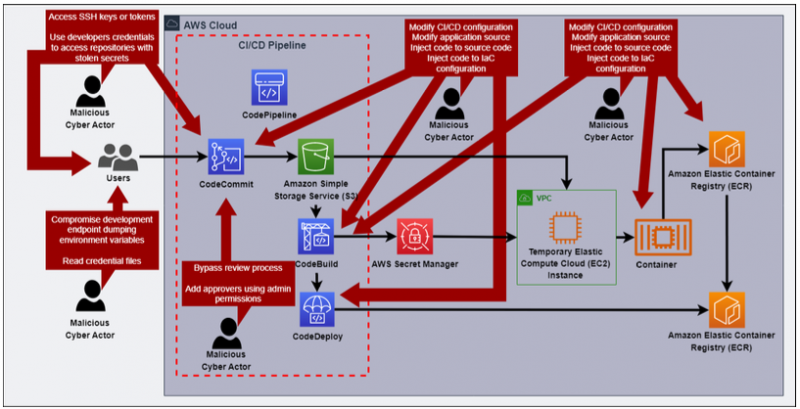
To prevent these scenarios, the memo has numerous specific recommendations, including using stronger cryptographic algorithms, shortening the certificates’ terms and managing their timely renewals, using secure code signing and verifying these signatures, using two-person rules to update all code, implementing multifactor authentication, deploying updated patching and software versions, and segmenting networks. In addition, there are several automated tools that can help to integrate security scanning into the pipeline, provide audit logs of code changes, and plan for resiliency in case of potential compromise.
Part of the problem with securing software pipelines is that there are so many entry points for an attacker, as the graphic above shows. Organizations need to understand code dependencies and how their application frameworks secure code.
They also need to make use of various ways, some of which are documented and suggested in the memo, that business teams can improve their software pipeline security posture. They include strengthening their authentication and access controls, implementing changes to their application development environments and tooling, and making changes to their software pipeline processes. Many of their recommendations are familiar to security professionals, but it’s worth reviewing the entire document because it can be easy to miss some.
After the 2021 Log4j-based attacks, I wrote an analysis for Infoworld on ways developers can make use of tools to harden their defenses. Just for that particular attack, there are dozens of them for various circumstances described earlier. CSOonline has this review of top automated application security tools from 2022. There are basically two kinds of these tools:
SiliconANGLE has covered various security providers who have new products and services to defend these CI/CD pipelines, including Cycode Ltd.’s Cimon, Cerbos, Google LLC’s deps.dev.API, ReversingLabs Inc.’s Software Supply Chain Security and Noname Security’s Discovery and Posture Management, just to name a few that were announced in the past several months. But many of the memo’s recommendations can be implemented without using any additional security tools by being thorough in plugging back doors and potential weak spots in the pipelines themselves.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.