 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Researchers at cybersecurity firm Wiz Inc. today detailed a newly discovered Python-based fileless malware that’s targeting cloud workloads.
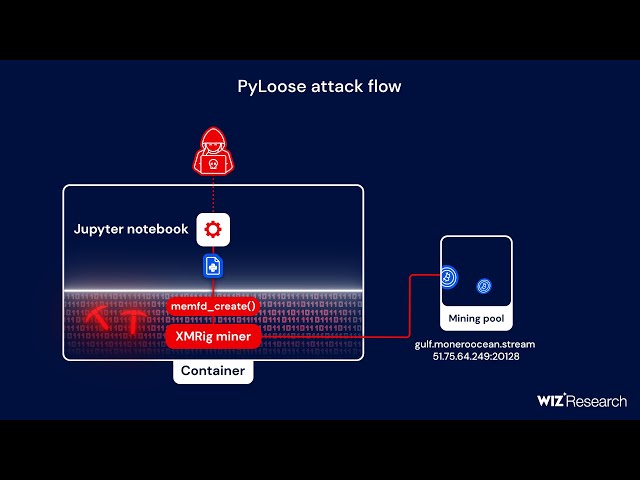
Dubbed “PyLoose,” the attack is said to be the first publicly documented Python-based fileless attack targeting cloud workloads in the wild. A fileless attack does not rely on traditional executable files to carry out an attack but instead exploits tools and features built into the target system’s software. Fileless attacks pose a significant challenge to conventional security solutions thanks to their evasion tactics.
The PyLoose attack leverages the Linux fileless technique, memfd, to load an XMRig Miner directly into memory. The attack circumvents the need to write payloads to disk by exploiting operating system capabilities.
PyLoose was first detected on June 22 and began with initial access through a publicly accessible Jupyter Notebook service. Those behind the malware then downloaded a fileless payload from a Pastebin-like website into Python runtime’s memory, bypassing the need for disk storage and optimizing the attack process by simplifying the command structure.
The researchers have been unable to link the attack to a specific threat group. However, they note that the use of an open data-sharing service to host the Python payload, adaptation of fileless execution to Python and embedding of XMRig miner configuration all suggest a highly skilled and knowledgeable threat actor.
While Pyloose may be the first documented Python-based fileless attack, there are actions that can be taken to protect against it. The researchers recommend that users should refrain from publicly exposing services like Jupyter Notebook, which may allow code execution. Robust authentication methods, such as using multifactor authentication as well as a centrally managed identity platform, can also provide further protection.
“These attacks serve as a reminder that organizations should have a security posture solution in place to help security teams eliminate toxic risk combinations, in addition to a runtime protection solution that quickly detects and responds to breaches,” the researchers concluded.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.