 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
A new, unpatched exploit that involves a sophisticated email phishing campaign has been discovered by security researchers at Guardio Labs.
The targets are Salesforce Inc. customers, and the threat involves spoofing the company’s email servers and domain names. The process of finding and fixing the issue reveals a lot about how security teams can work together to fight phishing.
Called PhishForce, the attack is quite clever, designed to avoid detection by both Salesforce and Meta Platforms Inc.’s Facebook. It uses an old technique: sending malicious emails and hiding them inside ordinarily trusted mail gateways so that the emails won’t be challenged by protective shields. The researchers found a single questionable email message, as shown in the screen capture below, that triggered their investigation.
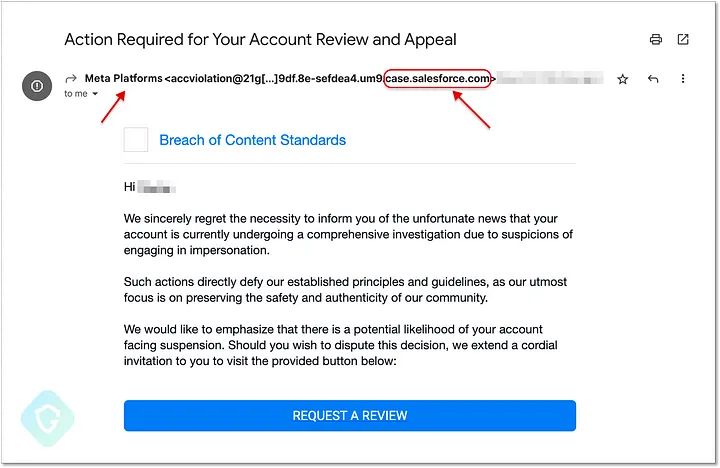
The circled part of the message shows an “@salesforce.com” domain, but labeled as coming from “Meta Platforms.” That should be the tipoff that this is a phishing email. The big blue button is also mislabeled with “Request a Review.” It doesn’t: By clicking on this button, a user is sent to a phishing page that’s designed to grab their Facebook account details.
The second tipoff is that the phishing page is hosted by Facebook and is supposed to be some sort of game. Yet the page has other content that has nothing to do with games. This is where the clever part comes into play: The malicious email has a legitimate link to facebook.com and is sent from a legitimate email address of salesforce.com, using its legit email gateway services. Essentially, the malicious email is hiding beneath this patina of respectability.
The researchers found that the attackers did something else that tied everything together. It took advantage of a trouble-ticketing system to use the email address “case.salesforce.com” – which normally is used to receive emails – but to send the emails instead.
This sounds simple, but the role reversal is key to how the entire attack happened. Guardio notified Salesforce at the end of June, and the vulnerability was fixed within a month and deployed across the company’s infrastructure. It also contacted Facebook, which then removed the malicious gaming accounts.
“The Salesforce security team was effective and responsive, taking these kinds of issues very seriously and prioritizing it accordingly,” the researchers said in their blog post Wednesday describing the exploit. “Bad actors are continuously testing the limits of email distribution infrastructure and existing security measures. [Service providers should] take proactive steps to keep scammers away from secure and reputable mail gateways.”
The battle against phishing will no doubt continue. The takeaway from PhishForce is to be always watching for elements that don’t quite add up, and also never to assume that email is harmless just because it originates from a legit domain.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.