 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
An aging core internet protocol is finally getting the ax by Microsoft Corp.
But it wasn’t just last month’s announcement that the software vendor was ending support for versions 1.0 and 1.1 of Transport Layer Security, or TLS, but that it was actually dropping the support from the impending release of the latest beta version of Windows 11.
TLS is one of those protocols that have far-reaching influence. It provides the security for encrypting web pages — designated with the “s” in HTTPS URLs for example. It also provides for encrypted connections used today in communications tools such as virtual private networks and secure command consoles called Secure Sockets Layer shells that operate numerous servers.
These protocol updates take time to develop, because they rely on a consensus approach with one of the internet’s international standards bodies. The latest version of TLS is 1.3, which was adopted in the summer of 2018, replacing version 1.2 which came out in 2008 and 1.0 which was released in 1999.
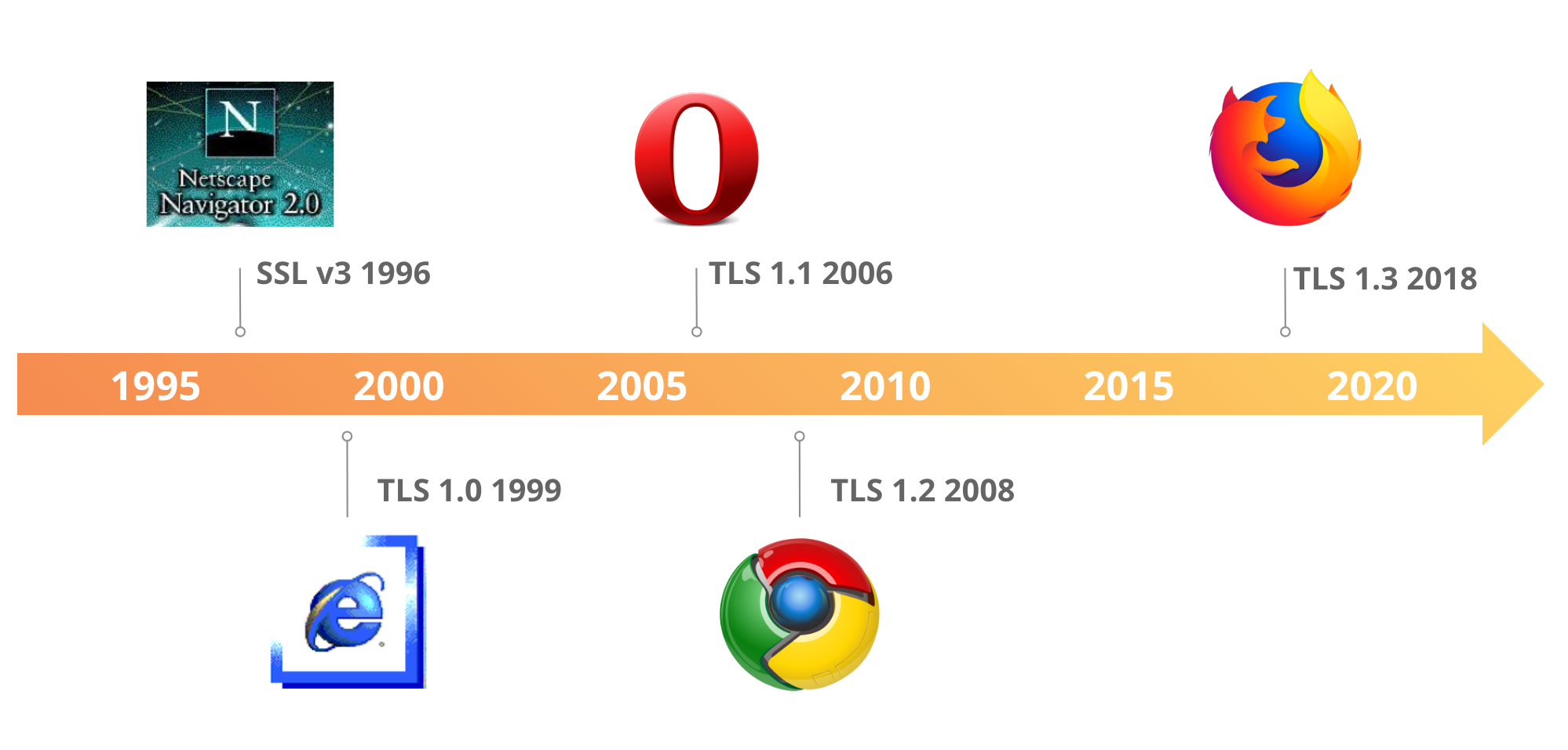
In the case of TLS 1.3, the process took five years from concept to implementation. Now most web traffic happens over HTTPS connections and we don’t give this much thought. The new version speeded up network conversations by reducing overall latency – version 1.2 required two round trips, while 1.3 needs only at most a single round trip — and made the “handshakes” between two computers a lot more secure, as illustrated in the accompanying diagram.

But just reducing latency wasn’t enough, and the older TLS version were vulnerable to attacks that were well-known and often used as initial exploits to penetrate networks, notoriously including 2014’s Heartbleed attacks for example.
Cloudflare summarized five of these vulnerabilities in their blog post several years ago, basically identifying the progress in improving encryption keys. The latest TLS 1.3 version “make it impossible for someone to enable the vulnerable aspects of TLS 1.2,” as they wrote in their blog, and this is why version 1.3 removed many legacy features.
The U.S. National Security Agency warned about these vulnerabilities back in 2021 and recommended that organizations block all use of TLS 1.0 and 1.1. Most of the major web browser vendors have dropped their support for these versions for several years. Microsoft said in its announcement that “we have been tracking TLS protocol usage for several years and believe TLS 1.0 and TLS 1.1 usage data are low enough to act.”
Nevertheless, there are still some places they are being used. The NSA warned, “Using obsolete encryption provides a false sense of security because it may look like sensitive data is protected, even though it really is not.” That is excellent advice.
Microsoft said it will disable support of TLS 1.0 and 1.1 by default in the new Insider preview build of Windows 11 that’s expected any day now and then in subsequent versions. But this doesn’t mean Windows can’t work with these aging protocols: Information technology administrators can turn this on with edits to the Windows Registry. That is somewhat time-consuming and painful, to be sure, and easily prone to mistakes.
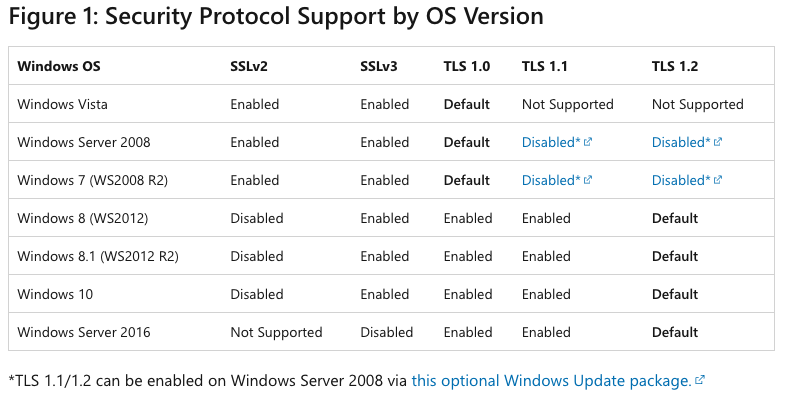
Microsoft acknowledged the older protocol versions might still be used by a variety of applications, such as in ancient versions of its SQL Server and pre-2018 Intuit Turbo Tax versions. They assembled a series of suggestions to customers who may have problems with removing other dependencies in this document posted with revisions last month, and summarized the support of the various versions across its older Windows operating systems in the accompanying table.
There have been numerous tools to help IT managers find and fix outdated TLS implementations. And even though Microsoft is still supporting TLS 1.2, it is probably a good idea to update these deployments to version 1.3, because eventually Windows will move on to that protocol too.
The NSA has a collection of mitigation tools and best practice suggestions including Snort signatures to locate old TLS versions, templates for web server configurations and various network scanners. These are open source and free. One of those tools is from Qualys’ SSL Labs that can test both browsers and server implementations of TLS.
TLS isn’t the only upgrade target for Microsoft’s cleanup campaign as of late. Last week, it announced the end of support for legacy third-party printer device drivers, a decision that will take several years to trickle down through the various Windows products. These drivers were another source of potential vulnerabilities, as this post from Sentinel Labs wrote about in 2021.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.