 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
IBM Corp.’s X-Force security consultancy annual 2023 Cloud Threat Landscape Report is out today, and it’s not a pretty picture.
Based on several collections of threat intelligence data compiled from June 2022 to June 2023, the report reveals that 82% of data breaches in its investigations involved various cloud data compromises. IBM found that cloud-related vulnerabilities have doubled since 2019.
More than a third of the incidents occurred from stolen user credentials. Even more depressing, each one of these could be obtained with an average cost of $10 across dark web marketplaces.
The most popular ones for sale are Microsoft Corp. Outlook cloud logins. These accounted for more than 5 million mentions, according to IBM’s partner Cybersixgill, which monitors these illicit locations. The distribution of various access types being monetized across the dark web are shown in the accompanying diagram.
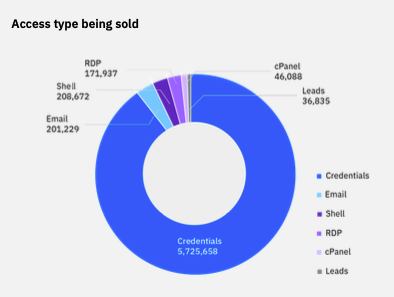
IBM saw a big jump in using compromised plain text cloud credentials this past year, accounting for more than a third of all reported incidents in the past year, up from 9% in the previous year. Many of these credentials were for service accounts that had additional access privileges, making them more attractive for criminals to move about a target’s network more easily. These accounts are also more difficult to track down since they aren’t directly tied to a particular user, at least not initially.
The report takes a dark turn: “Organizations tend to be more exposed than they realize, often underestimating the potential targets within their environment that can serve attackers’ objectives. Shadow IT and an unmanageable vulnerability debt makes it increasingly challenging for organizations to know where they are most exposed.”
Although cloud computing certainly has its advantages when it comes to flexibility and cost savings, it does also carry some drawbacks when it comes to how it is configured. “If implemented improperly, it’s possible to overlook an outdated application running in the cloud, or worse, be unaware that the application is even in use,” IBM states in its report.
One of the more interesting attacks observed by various IBM teams is called proxyjacking, by which adversaries can use space network bandwidth of a legitimate user for their own criminal purposes. Akamai researchers cited in this link also noted this method’s rise in their past summer’s threat report, saying it “has become the newest way for cybercriminals to make money from compromised devices in both corporate and consumer ecosystems.”
IBM has said that a big enough botnet could net an attacker hundreds of thousands of dollars per month in profits. One reason for its use is that hijacking network proxies doesn’t leave a telltale sign of increased processor usage, such as might be observed for any illicit cryptomining hijacks.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.