 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
CrowdStrike Holdings Inc. today announced new products extending its Falcon protection line and highlighted various threat research results from its annual Threat Hunting Report released last month.
Also announced at the company’s annual Fal.con user group conference was the acquisition of Bionic.ai for cash and stock for an undisclosed amount. The companies expect this transaction to close during CrowdStrike’s next fiscal quarter. Bionic has been in business for four years and is based in Palo Alto.
It uses an agentless approach to protecting applications by discovering vulnerable code dependencies and inventorying services and data usage. CrowdStrike will integrate Bionic into Falcon as well as continue to offer it as a standalone product. “Bionic shares our passion for customer-focused innovation and will make a great addition to the CrowdStrike team,” said George Kurtz (pictured below), co-founder and chief executive of CrowdStrike.
The company announced several extensions to its Falcon line of defensive products, adding to the more than 20 existing modules that have made the tool both popular and effective, especially among larger corporate customers. Almost two-thirds of their customers deploy at least five Falcon modules, according to their latest data. The new products include:
 Raptor will roll out over the next year with initial upgrades beginning later this month. Kurtz gave an interactive demo (shown adjacent) at the conference of how CharlotteAI could find and fix various vulnerabilities on a network of several thousand PCs running Windows, Linux and Macs.
Raptor will roll out over the next year with initial upgrades beginning later this month. Kurtz gave an interactive demo (shown adjacent) at the conference of how CharlotteAI could find and fix various vulnerabilities on a network of several thousand PCs running Windows, Linux and Macs.With these additions, CrowdStrike’s Falcon will get a boost to cover more of the security landscape, better incorporate AI-based techniques and compete with products such as Wiz’s cloud native tools and Google’s Chronicle, just to name two competitors who are already in this market space and leveraging AI.
One big advantage of Falcon is its combined agent/agentless approach that makes it easier to collect and analyze a lot of data. “Falcon provides a single, unified agent, managed from a single console, using a single backend data lake collecting information across endpoint security and data protection,” said Rajamani.
Falcon’s challenge for IT managers is being able to integrate the new components and for potential customers to share the collected data among the right staff members that have the skills to understand what they are seeing and to act on the alerts.
The threat report consolidates data from two previously separate threat analysis groups now called the Counter Adversary Operations team and headed by Adam Meyers. As part of the team’s duties, it keeps track of 220 threat actor groups around the world, including the more active state-sponsored attackers from Russia, North Korea, Iran and China.
 One of the biggest jumps in attack types was seen with kerberoasting attacks. This attack method is nearly a decade old and is so well-known that it has its own MITRE ATT&CK category. Nevertheless, last year CrowdStrike saw a sixfold increase across its network telemetry in this type of attack, with one-sixth of all attacks being attributed to the Russian Vice Spider malware group.
One of the biggest jumps in attack types was seen with kerberoasting attacks. This attack method is nearly a decade old and is so well-known that it has its own MITRE ATT&CK category. Nevertheless, last year CrowdStrike saw a sixfold increase across its network telemetry in this type of attack, with one-sixth of all attacks being attributed to the Russian Vice Spider malware group.
These target the Kerberos authentication protocols, whereby hackers extract encrypted tokens typically of service accounts and subject them to dictionary or brute-force methods to break the encryption. These service accounts have higher privileges that can then be used to compromise an entire Active Directory domain and launch further exploits.
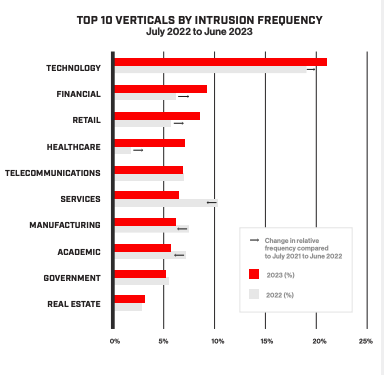
Meyers in a press conference webinar said that the biggest recipient of threats was the vertical segment involving technology-related businesses, as shown in the accompanying graphic. “This is a very lucrative vertical for cyber criminals, and it is targeted because it is force multiplier for supply chain attacks and other espionage techniques,” he said. “There is a continuing huge concern that tech companies will be a target.”
The company also saw a 300% increase in attacks involving remote management tools, and a 147% increase in advertising for access brokers across various dark web forums that it monitors. Finally, it saw attackers getting better at moving quickly to penetrate their targets, shaving five minutes off the average time in last year’s survey of 84 minutes to launch an attack.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.