 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
The U.S. Federal Bureau of Investigation and the Cybersecurity Infrastructure and Security Agency today released a joint cybersecurity advisory warning of the Snatch ransomware operation.
Snatch first appeared in 2018 and operates on a ransomware-as-a-service model. That’s a cybercriminal business model where ransomware operators develop and provide ransomware to affiliates who pay to use it for launching ransomware attacks. The first known victim in the U.S. of a Snatch ransomware attack was ASP.NET hosting provider SmarterASP.NET in 2019.
The joint advisory has been released to disseminate known ransomware indicators of compromise and tactics, techniques and procedures associated with Snatch ransomware identified through FBI investigations as recently as June 1, 2023.
Snatch threat actors are said to be consistently evolving their tactics to take advantage of current trends in the cybercriminal space and have leveraged the successes of other ransomware operations. Affiliates using Snatch have targeted critical infrastructure sectors, including companies and organizations in the defense, food and agriculture and information technology sectors.
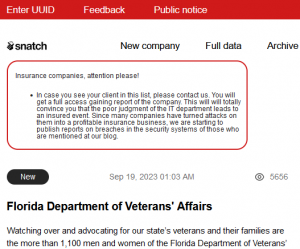
Snatch dark web site
Like many ransomware actors over the last few years, Snatch operates on a so-called double-extortion basis, both encrypting data and stealing it — demanding that a ransom be paid not only for a decryption key but also a promise that the stolen data will not be published on Snatch’s dark web site.
Recent victims of Snatch ransomware attacks, as listed on their dark web site (pictured adjacent), include the Florida Department of Veteran’s Affairs, Zilli, CEFCO Inc., the South African Department of Defense and the Briars Group Ltd.
Michael Mumcuoglu, co-founder and chief executive of posture management company CardinalOps Ltd., told SiliconANGLE that there has been increased activity by the Snatch ransomware group over the last 12 to 18 months as it has claimed responsibility for several recent high-profile attacks.
“A unique tactic used by the Snatch ransomware group leverages ‘stealthy malware’ that takes advantage of the fact that many Windows computers do not often run endpoint protection mechanisms in Safe Mode,” Mumcuoglu explained. “Snatch ransomware avoids detection by forcing infected hosts to reboot into Safe Mode.”
Nick Hyatt, cyber practice leader at cyber advisory and solutions provider Optiv Security Inc., said that he believes that CISA likely released this advisory about the Snatch ransomware group as part of its effort to be more active in the community.
“While we have not observed any change in Snatch’s tactics, techniques and procedures recently, per our research they are most active in North America, with a particular focus on the industrial vertical,” Hyatt added. “Between July 2022 and June 2023, we tracked 70 attacks by Snatch across all verticals. Overwhelmingly, those attacks were focused on North America.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.