 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
The malware group behind Magecart continues to be on the cutting edge of hiding in plain sight.
A report this week from Roman Lvovsky, an Israeli security researcher at Akamai Technology, demonstrates three obfuscation techniques that have been recently spotted by their telemetry. Magecart has been operating for years infecting various e-commerce websites, most notably those running Magento and WooCommerce. These new methods have targeted sites run by food and other retailers.
Magecart’s operators have a three-stage workflow that is shown in the diagram below. This makes it harder to detect and neutralize, since many code scanners won’t immediately flag the injected code. The workflow also makes it easier to hide the full attack infrastructure and command servers, thereby prolonging the attack.
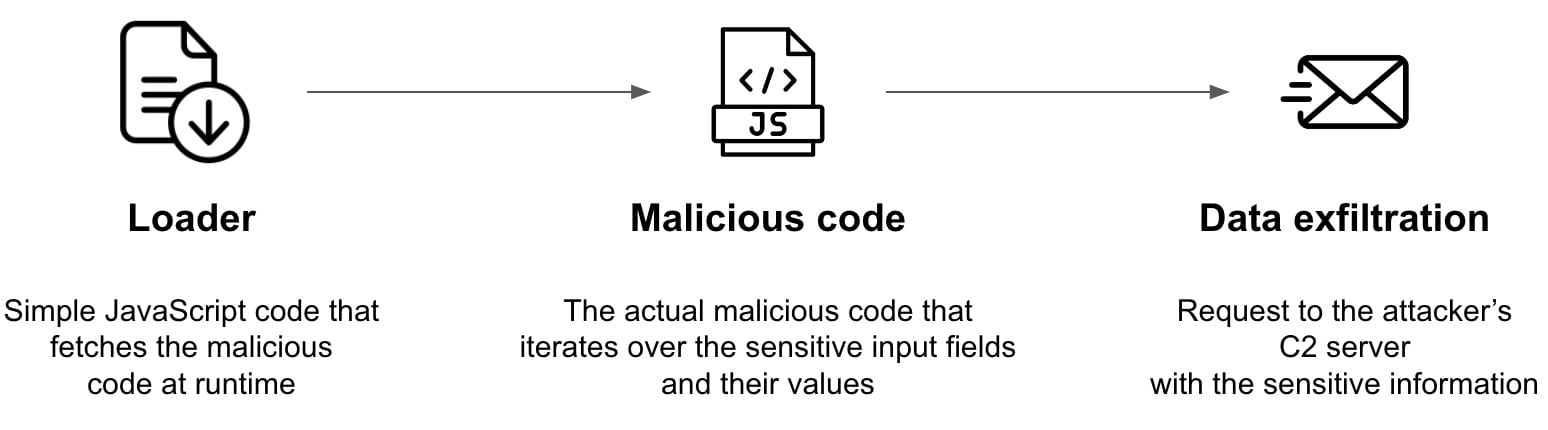
The malware uses the loader stage to directly insert its code into the web server’s pages. Subsequent stages are used to steal data, such as customer credit card numbers and passwords.
One of the techniques is novel and hasn’t been seen before, at least according to Lvovsky. “It really surprised us,” he wrote in his post.
The first-stage loader is disguised as a Meta Pixel piece of code, a legitimate Facebook visitor and advertising tracking service that’s employed widely. The piece of code easily eludes malware scanning tools.
What makes this technique dangerous is that later stages appear to summon the 404 error page of a bad URL location. Although these pages are frustrating and seen often by web visitors, this page carries a hidden piece of the malware. “It was initially confusing and made us wonder if the skimmer was no longer active on the victim websites we found,” he wrote.
But a thorough search through the 404 code found the actual attack processes hidden in a comment string. What Lvovsky found was that the attacker had alerted the default 404 error page script so that any website error would bring up the infected page. This is quite clever and shows that it can be accessed by a variety of tools used by Magecart operators to conclude their attacks and steal data.
One of the reasons for Magecart’s staying power is that its operators are continuously evolving their attack methods, becoming more sophisticated and dangerous in finding better evasion methods. Perhaps now users will examine even their error pages for potential threat sources.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.