 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
A new report from cybersecurity software firm Malwarebytes Inc. today details a “malvertising” attack that exploits Google LLC ads to trick users into visiting a fake site for the open-source password management KeePass.
Described by the Malwarebytes Labs researchers as “clever,” the attack methodology involves the attackers impersonating the official KeePass website using the Punycode character encoding system to allow them to register domains that visually appear very similar to legitimate ones. The difference between the original and fake sites is said to be visually so subtle that it will undoubtedly fool many people.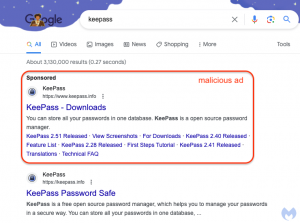
Setting up a fake domain is one thing, but getting accepted in Google Ads is another level and this is what has happened here. The attackers managed to get the fake KeePass site not only into Google Ads but also to appear at the top of search results. The malicious Google ads look entirely genuine and feature the official KeePass logo and URL.
When clicked, the ad redirects users via a cloaking service to a decoy site with the domain ķeepass[.]info, using Punycode. Easy to miss, there’s a tiny character beneath the “k” that is not a standard letter k but one from another character set. Because it’s easy to miss, users are none the wiser that they may not be on the official KeePass site.
While not an exact replica of the original site, the fake KeePass is still convincing and offers unsuspecting visitors a malicious .msix installer that is digitally signed. Inside the malicious installer lies PowerShell code linked to the FakeBat malware family. The malware subsequently communicates with a control server and prepares the victim’s device for future malicious activity.
“While Punycode with internationalized domain names has been used for years by threat actors to phish victims, it shows how effective it remains in the context of brand impersonation via malvertising,” the Malwarebytes researchers note. “Users are first deceived via the Google ad that looks entirely legitimate and then again via a lookalike domain.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.