 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
The Iranian hacking group Scarred Manticore, which has been linked to the country’s Ministry of Intelligence and Security, has been secretly running a digital spy ring across the Mideast.
It has targeted government and large infrastructure companies such as telecom and financial services to steal data. A new report Tuesday from Check Point Software Technologies Ltd.’s research arm describes how the group’s tactics have become more sophisticated, using custom-made hacking tools to penetrate various networks, compromise web servers and avoid detection.
The hackers gained access to a wide variety of digital content, including emails and web transactions, and used their malware to snoop on various government and private sector conversations to conduct espionage and map out the network infrastructure that could be used to hone future attacks. The report wasn’t specific about what data was stolen, but did mention incursions in Saudi Arabia, Jordan, Kuwait, Israel and Oman.
At the core of its hacking tool, which Check Point calls Liontail, is a corrupted web software system driver that takes advantage of hidden features and can blend in with normal network traffic. Researchers typically find relationships and connections to other hacking groups by examining their malware code but Liontail appears to be something unique.
Moreover, it’s customized to each particular web server that it targets. The researchers found other hacking tools that are also being used by the group behind OilRig but did not conclusively say whether they are actually the same entity. Israeli security officials, quoted in the New York Times, confirmed that Liontail has been active in their country over the past several months.
The researchers provided a detailed technical description of the malware framework, diagrammed below, in another blog post.
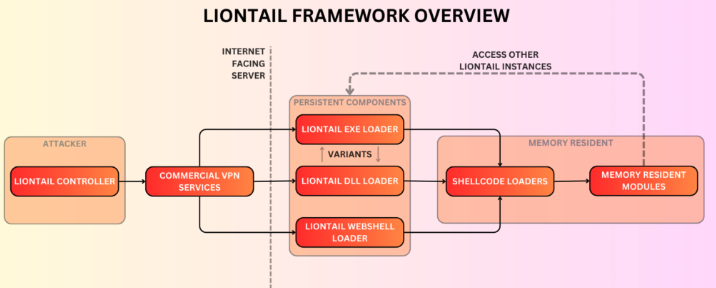
The Check Point analysis confirms an earlier blog post from Cisco Systems Inc.’s Talos threat researchers that was posted in September. They labeled the exploit HTTPSnoop and PipeSnoop and found the malware masquerading as the Windows software agents of the Palo Alto Networks Inc.’s Cortex anti-malware product. This interacts directly with the web device drivers or named pipes system calls, respectively — hence the two different labels — and can observe and interact with the web traffic to launch malware attacks.
Check Point researchers, who collaborated with Sygnia’s incident response team, have been watching the Manticore group’s output since 2019. They can track the group’s activities to an attack on the Albanian government back in 2021-2022, when it compromised a Microsoft SharePoint server and stole a large quantity of police data. That attack prompted Albania to break off diplomatic relations with Iran.
What’s troubling about these current attacks is showing how far the group has progressed from its humbler beginnings, when it used very simple exploits, such as injecting malware and creating backdoors to Windows web servers with open-source proxy servers that depend on Microsoft web server and .Net frameworks.
Its latest and most sophisticated campaign was detected this summer and had been operating stealthily for at least a year. This malware makes use of lower-level system calls and provides a great deal more flexibility and obscurity. “The recent Liontail framework represents a leap in sophistication compared to their earlier activities, showcasing the continual refinement of Iranian cyber capabilities,” Check Point researchers said.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.