 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Palo Alto Networks Inc. today added new artificial intelligence-related security features to its Cortex security automation and intelligence product line — the key word being “automation,” especially when it comes to finding and stopping threats and exploits.
The average time to discover and contain an incident takes five and a half days, according to the company. And remediation is stretching this time lag even further, thanks to a plethora of security products operated by disparate teams with silos of data that aren’t typically shared across an enterprise. On top of that, many of the current security operations products still require manual methods to sift through the alerts and track down their implications.
Cortex XSIAM v2.0 now has the ability to add any machine learning framework to Cortex, which is something many of the company’s enterprise customers have asked for since the AI explosion of the past year. It’s accomplished using the open-source Jupyter Notebook tool.
What this means is that the petabytes of network telemetry that Palo Alto collects daily is now available for these models to enable better fraud detection or data visualization, all in the service of cutting down the time an attacker has between compromise and execution. One oil and gas customer was able to reduce by 75% the number of false positive alerts.
According to Paul Alexander, director of information technology for Imagination Technologies, it could close all of its open security incidents with the new features. Previously it was only able to close a 1oth of them. He likes Cortex “because it effectively lets us cut straight to the real and serious incidents that we need to focus on and we’re not wasting time on data that doesn’t need our attention.”
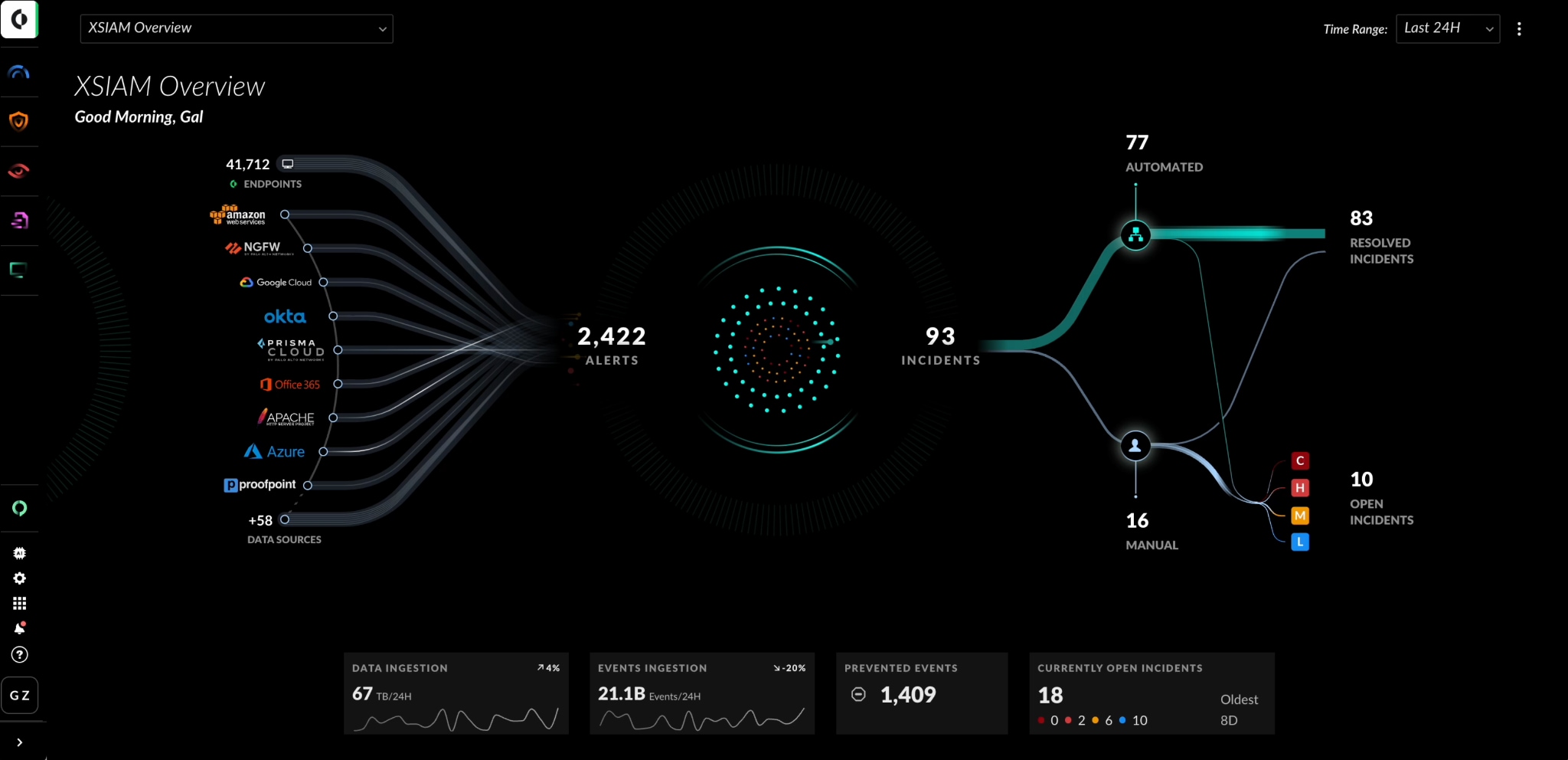
Cortex will also add a new Command Center module so that security operations staffs can more capably monitor alerts and prioritizing of research subjects. This dashboard is designed to answer questions such as what data set is being analyzed, the number and types of open incidents, and the number of prevented threats. It comes with a nice visualization of the workflows involved in remediation and removal of threats (pictured below), and also includes a separate dashboard to map threats to the MITRE ATT&CK schema.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.