 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
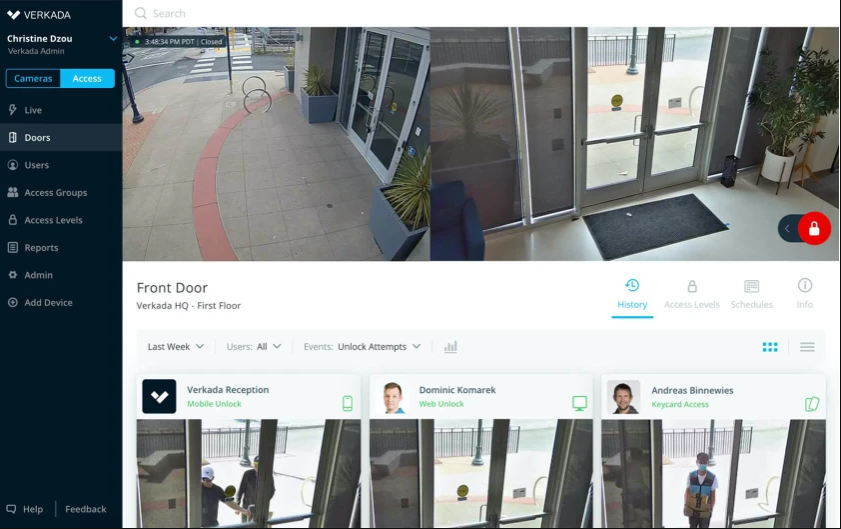
Verkada Inc., a Silicon Valley-funded security camera startup, has suffered a data breach with hackers reportedly able to gain access to 150,000 live camera feeds from companies, jails, police departments and schools.
The data breach was led by an “international hacker collective” and intended to show the ease with which systems could be broken into, a spokesperson for the collective Tillie Kottmann told Bloomberg today.
Kottmann has been linked to previous hacks in the past, including releasing data stolen from Intel Corp. in August. Kottmann said its reasons for hacking are “lots of curiosity, fighting for freedom of information and against intellectual property, a huge dose of anti-capitalism, a hint of anarchism – and it’s also just too much fun not to do it.”
The hack is claimed by Kottmann to be relatively simple. The hacking collective gained “Super Admin” level to Verkada’s system using a username and password found publicly on the internet. With access gained, they then accessed the entire company’s network, including root access to the cameras including those belonging to some customers.
Verkada, founded in 2016 and funded by venture capital firms including Sequoia Capital, counts among its customers Tesla Inc. and Cloudflare Inc., both of which had their security cameras compromised. Other security cameras compromised included those belonging to Equinox gyms, Halifax Health in Florida, a police station in Stoughton, Massachusetts, the Madison County Jail in Huntsville, Alabama, the Graham County detention center in Arizona and Sandy Hook Elementary School, the site of a mass shooting in 2012.
A representative for Verkada said in a statement that “we have disabled all internal administrator accounts to prevent any unauthorized access” and that “our internal security team and external security firm are investigating the scale and scope of this potential issue.”
“Verkada positions itself as a ‘more secure, scalable’ alternative to on-premises network video recorders,” Rick Holland, chief information security officer at digital risk protection software company Digital Shadows Ltd., told SiliconANGLE. “The Verkada intrusion is an example of the risks associated with outsourcing services to cloud providers. You don’t always get more secure when you outsource your security to a third party.”
The video leak is likely to result in investigations from the Department of Health and Human Services for regulatory violations because surveillance footage can be considered protected health information, Holland added. “GDPR violations of personal data could have also occurred, and class action lawsuits could also be on the horizon,” he said.
Hank Schless, senior manager of security solutions at mobile security solutions provider Lookout Inc., said it’s likely access was gained through a phishing attack that was made more convincing through social engineering.
“Targeted phishing attacks are known as spearphishing attacks,” Schless explained. “Malicious actors will oftentimes use publicly available information in places such as social media profiles to build a convincing campaign targeting an individual.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.