 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Hackers are reported to be actively targeting WordPress sites with unpatched versions of the Tatsu no-code page builder plugin installed.
Detailed Monday by Ram Gall at Wordfence, the large-scale attack is targeting a Remote Code Execution vulnerability in Tatsu that was publicly disclosed in March. Although an updated version of the plugin has since been released, as is often typical with software or, in this case, a WordPress plugin, not all users have installed the latest version. That opens the door to hackers.
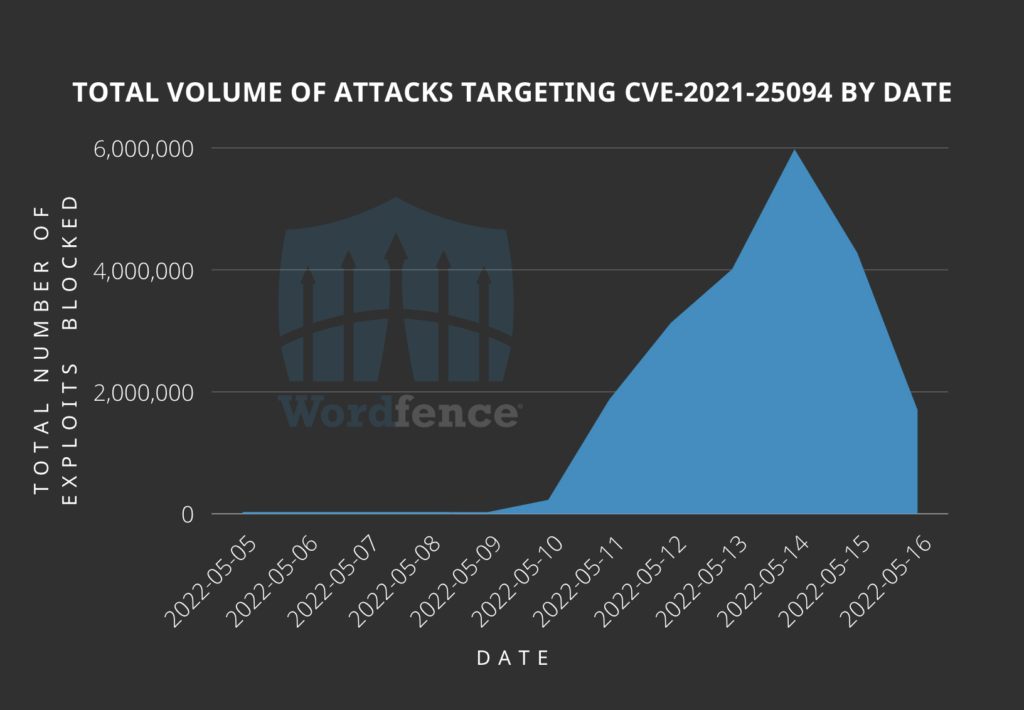
The exact number of sites running unpatched versions of Tatsu is unknown but could be as high as 50,000. What isn’t hard to track is the number of attacks: Wordfence saw a peak of 5.9 million attacks against 1.4 million sites on May 14.
The attack volume has since declined, but the attacks are still ongoing. Most of the attacks are described as probing attacks to determine the presence of the vulnerable plugin.
If a WordPress installation is running an unpatched copy of Tatsu, the most common payload deployed is a dropper, software that allows additional malicious scripts to be installed in a randomly named subfolder.
The obvious solution to the problem is for Tatsu users to update the plugin to the latest version, currently 3.3.13. It’s warned that an earlier update, 3.3.12, contained only a partial patch that did not fully address all issues.
“When it comes to cybersecurity, most organizations give little thought to their websites,” Chris Olson, chief executive officer of digital safety provider The Media Trust, told SiliconANGLE. “The Tatsu vulnerability shows us why this is a mistake: Websites, which play a key role in marketing and revenue generation, are increasingly targeted by hackers, making them a source of risk to customers and casual visitors.”
Olson noted that as a precaution, anyone managing an organization’s website should be performing regularly scheduled maintenance that includes updates for plugins and security patches.”This is all the more true if it runs WordPress or another open-source CMS that depends heavily on third-party code, as these are chief drivers of risk,” Olson said.
THANK YOU