 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
When most people think about cyberattacks, they might think of phishing emails or hackers targeting company servers, but a new report explores how attackers are now targeting scanner notifications.
Detailed today by Jeremy Fuchs, a researcher at cloud email and collaboration security firm Avanan Inc., a Check Point Software Technologies Ltd. company, attackers are spoofing scanner notifications to send malicious files. Those behind the attacks are sending spoof scanner notification emails to users informing them that they have received a scanned message.
Fuchs explains that with some scanners, an email notification is created to allow users to download a scanned file. While noting that scanning is much less common in the work-from-home era, it’s not unheard of and, as a result, when people receive such messages, they may believe it is legitimate.
In one example, a subject line read “Commission Receipt” as a hook to have recipients click on the email and attachment. This is where social engineering comes into play as end-users see something of high value, such as their next paycheck, and may click without thinking twice, giving the hackers a quick win. Even if users don’t expect to see an email from a scanner, they will often look at the convincing subject line and click on the file.
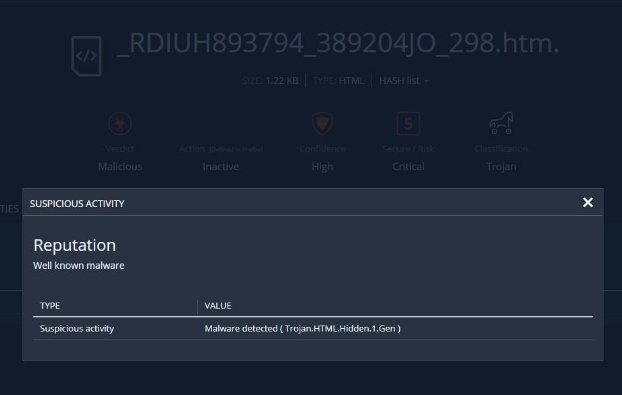
Not surprisingly, the attached file is not as it seems and is instead an .htm file that includes a malicious Trojan virus that attempts to take over the user’s computer.
“Though the email appears benign, it underscores the importance of analyzing all files upon downloading,” Fuchs explained. “By scanning attachments for malicious content, users can feel more confident that the attachment is actually safe.”
The report concludes with advice that applies not only to potentially fake scanner notifications but to all emails. Email users are advised to always look at the sender’s address, be cautious when downloading .htm files since they can be used for malicious content and, if ever unsure about an email, ask the original sender.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.