 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
A group of North Korean hackers group continues to threaten networks and businesses around the world, now with ever more sophisticated new attacks.
Lazarus has been behind some very nasty exploits, including the double software supply chain attack on 3CX this past March and one of the largest thefts of cryptocurrency from the Ronin Network in March 2022. The group also is one of those that took advantage of Log4j vulnerabilities in 2022 as well as behind the 2017 WannaCry ransomware attacks that paralyzed many around the world.
What makes Lazarus lethal is that it’s continually improving its criminal network and climbing to new technical heights. And indeed, in July, according to Bleeping Computer, the group hijacked Microsoft IIS web servers to spread its malware to spread so-called watering hole attacks that leverage a trusted website to infect visitors.
Just last week, Cisco/Talos researchers published two reports on the group’s activities. “Lazarus Group appears to be changing its tactics, increasingly relying on open-source tools and frameworks in the initial access phase of their attacks, as opposed to strictly employing them in the post-compromise phase,” the researchers wrote.
Various analysts have called attention to this ploy, saying it’s the first state-sponsored hacking group that has been observed using open source in this manner. That is a new and diabolical twist to create a new strain of its remote access Trojan malware family that it has used previously, called CollectionRAT. The new strain so far has been targeted at both healthcare firms as well as main-line internet providers.
The new malware joins QuiteRAT and the older MagicRAT strains. These have targeted Zoho’s ManageEngine SaaS products, specifically a known vulnerability in the help desk app called Service Desk. Zoho claims these apps are used in the vast majority of Fortune 100 organizations. Back in January, Rapid7 announced the vulnerability, and warned it was being actively exploited despite being patched in November 2022.
In the past Lazarus hackers have used “a combination of social engineering and malicious package dependencies to infiltrate their software supply chains,” Yehuba Gelb of CheckMarx Security said in an August 2023 blog.
The social engineering tactics have been documented by Feross Aboukhadijeh, a researcher at Socket in July 2023. One path is to establish contact with a victim via WhatsApp, then build rapport and make the victim download malware from an infected GitHub repository.
Talos researchers identified the particular open-source framework called DeimosC2, and found that it reused some of the computing infrastructure they had already identified from previous MagicRAT campaigns. They outlined the logic flows among the variations in the screen capture below.
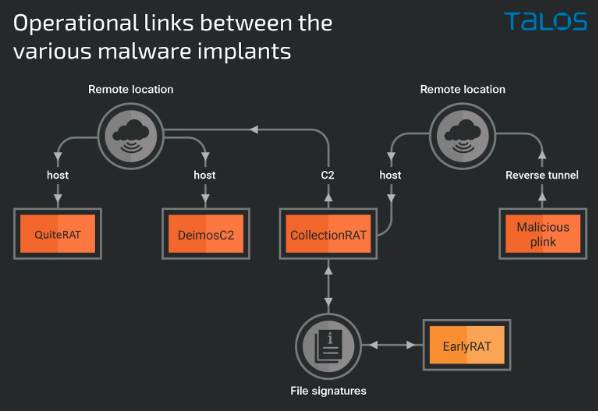
All these Trojans share the same functions, including running arbitrary commands, download new malware and managing files on the infected computers. The DeimosC2 framework replaced an earlier collection of custom code to establish persistence, set up reverse network proxies, and other mischief.
Talos links to an analysis of the framework done by Trend Micro last year. One possible reason for its use is that network defenders are on the lookout for other command-and-control frameworks that are more easily identified. Trend Micro writes that “criminals have been looking for alternatives to Cobalt Strike that provide many of the same functions” but is more difficult to detect.
The QuiteRAT malware is a smaller — 5 megabytes versus 18 megabytes — and more nimble version, and uses various code obfuscation techniques. Lazarus’ malware has a feature to gather device data and then go to sleep to hide from network scans. Talos researchers found three Lazarus-sponsored campaigns in the past year, so they continue to wreak havoc across the world.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.