David Strom
Latest from David Strom
Rapid7’s security chief Jaya Baloo: Break up silos to lock down cybersecurity
Not many chief security officers will point out not one but two times they took a job while their companies were under attack. But this is what happened to Jaya Baloo, who is now chief security officer at cybersecurity provider Rapid7 Inc. Even more interesting, she considers both times — which happened at two different ...
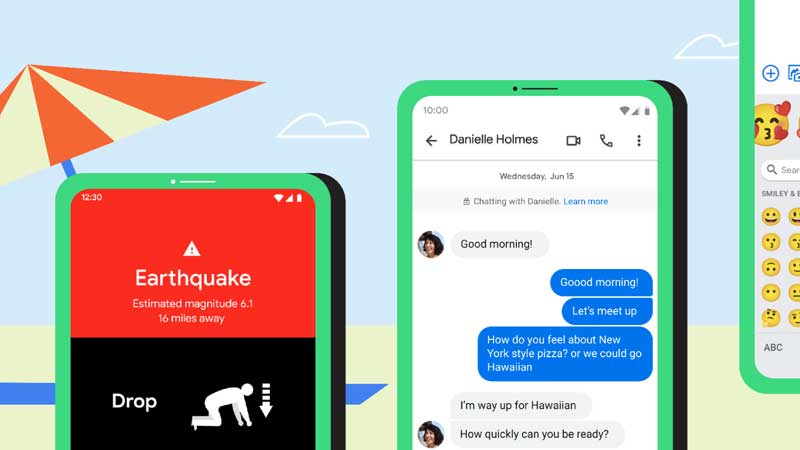
Android 14 to provide new security features for enterprise users
Google LLC Tuesday announced new security features for its upcoming Android 14 release that it claims will be a first for any mobile operating system provider. The features include the ability to disable 2G network access and another one to control access to encryption settings. Both are benefits for cell security, but they require managed ...
The rise of EvilProxy phishing malware
EvilProxy is once again on the rise. The malware is one of the more popular phishing kits that is used to bypass multifactor authentication by stealing credentials. A new report by Proofpoint Inc. today illustrates its new rise in popularity and its focus on compromising Microsoft 365 accounts of C-level executives at major corporations. These kits ...
Prioritizing cyberattacks still needs a lot of work, according to new Picus Labs report
Organizations aren’t very effective at prioritizing and preventing cyberattacks, according to a new study released today by Picus Labs. Picus Labs’ parent company sells attack simulation tools, and the study, The Blue Report 2023, is based on telemetry from 14 million simulations created by its customers from January to June 2023. On average, organizations’ security controls prevent ...
New cyberattack method: tracking typing remotely via keyboard sounds
A group of British cybersecurity researchers has figured out a novel new attack method: recording the sound a computer keyboard makes. The researcher took recordings using a nearby smartphone of typists and used it to train a sound classification model, achieving accuracies of 95% to suss out the actual keys pressed. They call this an ...
CISA: Beware of the malicious boot loader
The U.S. Cybersecurity and Infrastructure Security Agency has issued a call to action to beef up security of a little-known but important piece of software that can be found in every computer. Called the Unified Extensible Firmware Interface or UEFI, it is run at boot time and controls the operation of the computer, loads device drivers ...
Alarming survey: Many tech experts fail a test of their cybersecurity knowledge
A new survey of more than 2,300 self-identified technologists from 90 countries finds a glaring lack of cybersecurity knowledge. Conducted in April and May on behalf of RSA Security LLC, the survey asked a series of fact-based questions, such as the most frequent data breach cause and how to implement a zero-trust strategy. The results ...
ANALYSIS
What’s behind the never-ending rise of online payment technologies
Amid the ups and downs of e-commerce over the years, online payment technologies continue to evolve and thrive — and lately they’re nothing less than a thriving scene of continued innovation and transformation, thanks to a series of converging trends and a continuing series of corporate acquisitions. This progress has been helped by several factors. First, the ...
PhishForce: New phishing attack involving Salesforce and Facebook uncovered
A new, unpatched exploit that involves a sophisticated email phishing campaign has been discovered by security researchers at Guardio Labs. The targets are Salesforce Inc. customers, and the threat involves spoofing the company’s email servers and domain names. The process of finding and fixing the issue reveals a lot about how security teams can work ...
ANALYSIS
Google’s Web Environment Integrity project raises a lot of concerns
Earlier last month, four engineers from Google LLC posted a new open-source project on GitHub and called it “Web Environment Integrity.” The WEI project ignited all sorts of criticism about privacy implications and concerns that Google wasn’t specifically addressing its real purpose. Remember the problems with web cookies? WEI takes this to a new level. ...