David Strom
Latest from David Strom
Akamai research finds more sophisticated phishing threats in hospitality industry
New research from Akamai Technologies Inc. shows the increasing level of sophistication that attackers will use on a series of phishing attacks targeting hospitality websites. The attacks began as early as June 2023 and focused on exploits of the Domain Name System protocols. The attacks involve new efforts to hide their origins and also add ...
Cisco issues new fixes for second IOS XE vulnerability
Cisco Systems Inc. was busy last week shoring up the security of its IOS XE routers and switches as a vulnerability in their web user interface allowed remote attackers to gain control over some these systems, which could number around 40,000. The web interface to manage is used to provision and configure the device as well ...
FBI takes down 17 websites used in massive North Korean hiring scheme
The Federal Bureau of Investigation has seized 17 websites that it claims were used to recruit and hire thousands of phony information technology workers from North Korea. The seizure, announced Wednesday, is part of a continuing effort to grab monies collected by the phony hires in a massive fraud effort to evade U.S. sanctions and ...
A new hackathon is helping to make elections more secure
Most hackathons don’t take five years to schedule, but this one was for a good cause and worth the wait. Last month a group of hackers and vendors came together in a suburban Virginia office to try to improve the operations of various election computing devices. It comes at a moment in time when trust ...
SPECIAL REPORT: GENERATIVE AI TRANSFORMS EVERY INDUSTRY
How companies are scrambling to keep control of their private data from AI models
Ever since artificial intelligence and large language models became popular earlier this year, organizations have struggled to keep control over accidentally or deliberately exposing their data used as model inputs. They aren’t always succeeding. Two notable cases have splashed into the news this year that illustrate each of those types of exposure: A huge cache ...
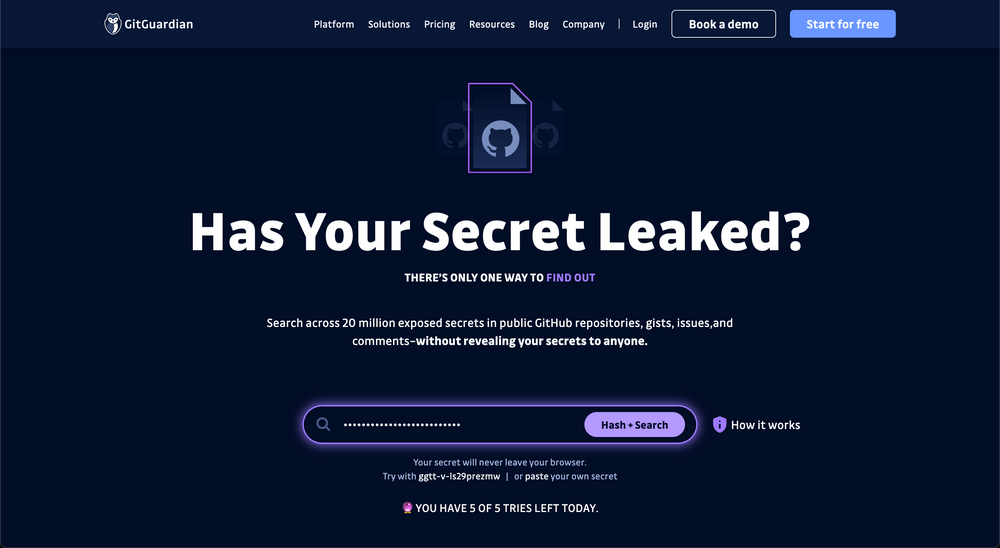
GitGuardian debuts new way to manage software encryption keys and secrets
Managing various encryption keys and other secrets has always been painful for enterprise security managers. A new service from GitGuardian called Has My Secret Leaked attempts to bring some clarity in a market that is typically overlooked by many corporate application developers. Ignorance brings peril, as can be most recently seen with Microsoft’s Storm-0558 breach ...
COMMENTARY
It’s time to put an end to the NTLM network authentication protocol
An ancient network authentication protocol has received its first death notice. The protocol, which has roots going back to the first local area network days of the 1980s, is called Microsoft NTLM, which stands for New Technology LAN Manager. Microsoft Corp.’s Matthew Palko charted its evolution – and hopeful eventual demise — in a blog ...
The Hamas-Israeli war is also being fought in cyberspace
The war between Hamas and Israel is also raging across the cybersecurity realm, with various malware exploits, disinformation campaigns and recruitment of citizen hackers seen on both sides of the conflict. It’s difficult to obtain independently verified information because of the dynamic situation, and because many Israelis have been deployed to active duty since the war ...
New Magecart malware concealment tactics, hiding inside web status page
The malware group behind Magecart continues to be on the cutting edge of hiding in plain sight. A report this week from Roman Lvovsky, an Israeli security researcher at Akamai Technology, demonstrates three obfuscation techniques that have been recently spotted by their telemetry. Magecart has been operating for years infecting various e-commerce websites, most notably ...
Distributed denial-of-service attacks are growing bigger and more lethal
A sad and scary new record was set this past week, with the latest and biggest distributed denial-of-service attack. The network security provider Cloudflare Inc. posted on its blog today that it had observed and repelled the attack in August. The previous volumetric record was set in February, the August attack was three times as much. ...