John Casaretto
Latest from John Casaretto
Healthcare site under continued attacks
Reports have been publicly trickling in that show some of the fears people have had thus far about the state of security for the healthcare.gov website. Critics have been pointing out how the site’s issues with stability, speed and reliability indicate a development process that could not possibly be considered secure. The obvious has been ...
NSA malware infects 50,000 worldwide computer with 1,000 hackers
Another week, more NSA developments, well allegations really. Somehow perhaps people are getting numb to these things as they come out there is less and less surprise left. Last week news emerged that the NSA had infected more than 50,000 computer networks around the world with a specialized piece of malicious hardware that was designed ...
Healthcare.gov moving to HP from Verizon Terremark
Trying to make sense of Healthcare.gov through everything that’s happened so far in this botched atrocious rollout, it’s quite mind-boggling. Now comes yet another head-scratcher. The Department of Health and Human Services has confirmed that Healthcare.gov will be picking up the tent stakes from its current Virginia home over at Terremark, a subsidiary of Verizon ...
CyberSecurity 2014 with Alert Logic
CyberSecurity. 2014. What is going to be out there in terms of threats, products and trends? There’s plenty of opinions about this because security in the industry is so widespread by disciplines. That’s the modern security environment. So we sought out companies in leadership positions, we sought out the people that are out on the ...
2014 Cybersecurity Forecasts
On a bit of a programming note, all month long in the month of December, SiliconANGLE will be featuring cybersecurity stories that focus on 2014 and beyond. We have gathered a number of thought leaders, executives and leading engineers to formulate a security picture of the year ahead. Security is as serious as ever. Cybercrime ...
The NSA wiretaps possibly behind Yahoo and Google surveillance
It seems the NSA stories insist on staying at the top of the tech radar. As found in a New York Times article, the NSA may have tapped into fiber-optic connections to achieve their eavesdropping operations. If that is the case, then this represents a significant physical breach has taken place. On top of all ...
‘Doomsday’ cache feared to be part of the Snowden files
Like the plot of a number of popular espionage action flicks, the action has now turned its focus to one set of the files within the Edward Snowden payload. They’re calling it the “Doomsday” cache – a highly sensitive, ultra-classified set of documents that some believe Snowden has stored into a data cloud. The document ...
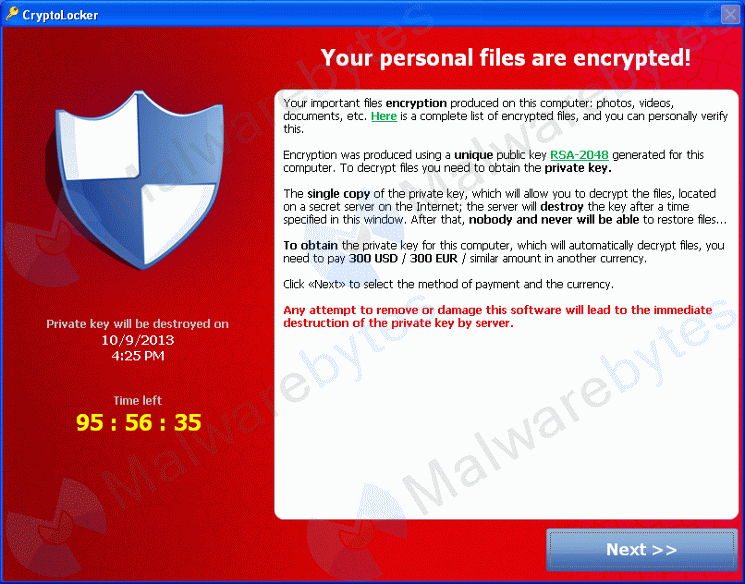
CryptoLocker malware encrypts your files, then sells you the key for Bitcoins
What do CryptoLocker and Healthcare.gov have in common? Well, they’re both big, they are both affecting a lot of people, and there’s a lot of nasty code in both of them. Not to start a trend here, but perhaps at some point starting now every technology disaster and threat will be likened to the steaming ...
[24]7 study reveals modern consumer disconnects
[24]7 has unveiled some leading research that sheds light on the new expectations that consumers bring to the enterprise. With the accelerating adoption of smartphones, today’s consumers engage in stops and starts across multiple channels and devices. These new parameters of engagement have changed consumer expectations as they now demand contextual customer service delivered on ...
What the security industry is missing from the new PCI 3.0 regulations
If you haven’t heard the PCI Security Standards Council has put forward the newest version of its compliance measures, PCI 3.0. The payment processing industry regulations come into effect Jan 1st and they cover some interesting new elements. This latest update adds a number of new measures to address the ever evolving landscape of technologies ...