John Casaretto
Latest from John Casaretto
A little spring cleaning can help protect children online
It’s 2014 and if it isn’t obvious enough, the internet is everywhere and children are all over it as much as the next group. At school, on mobile and especially at home, children are connected by game consoles, smartphones, educational software, email and on and on. Unfortunately many studies cite an alarming frequency at which ...
The rise of Data-Centric Security
Big Data is big news everywhere. As data grows, it is the holder of great promises for companies everywhere. What it’s doing is transformational, delivering the ability to deeply and quickly analyze information, delivering a new level of insight, and giving companies competitive advantages that were previously out of reach. On the flip side of ...
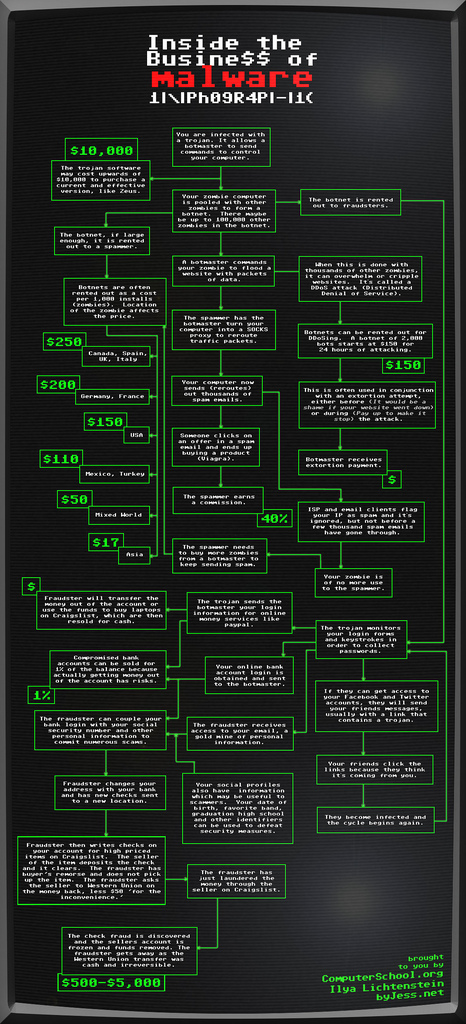
A different perspective on malware activity – BitSight Technologies
Stephen Boyer, CTO and Co-Founder of BitSight Technologies has a different perspective on malware activity. In the following guest post he introduces research from his company’s team of data scientists and provides analysis of global activity based on IP addresses. What’s interesting about this analysis is that rather than plotting malicious activity on a global ...
Exclusive: John McAfee in Belize, land of pirates.
If you think you know the John McAfee story by the accounts of the mainstream press, it sounds ultra-sensational. That’s how it seemed to me before I spent time interviewing John McAfee and subsequently spending time verifying his claims. At the same time, you don’t have to throw out all the saucier elements, either. Things happened: ...
HP PwnOwn hack contest wraps up, >$850K bounty for Chrome, IE, Flash exploits
The Pwn2Own hacking contest wrapped up this week and the big news is that this was the biggest such event ever. The event is run by HP’s Zero Day Initiative (ZDI), and it challenges security researchers to demonstrate flaws in popular consumer and enterprise software platforms. HP analyzes the information disclosed at Pwn2Own to improve ...
Privacy-Plate protects your car from being tracked
72 hours left to go in a very interesting IndieGoGo campaign. The product in this campaign is called Privacy-Plate and it’s designed to protect the privacy of not only you, but your vehicle. You would think, who cares about your car, right? The fact of the matter is that invasive tracking is happening everywhere you ...
Exclusive: John McAfee’s ultimate hack
Truth is indeed stranger than fiction, and this story is about as strange as it could be. For all the computer virus infections that John McAfee’s software may have prevented over the years, there has been one situation the man himself was unable to escape unscathed. He may however be having his day now. This Op/Ed ...
10 tips to align IT and security with the business
Reflect on the following and see if this seems familiar. Security teams exist in order to protect the business, while IT operations are focused on keeping systems up and running. You will also find application teams in the mix whose role is to ensure application consistency, availability and performance. The overlap between these teams can ...