Mike Wheatley
Latest from Mike Wheatley
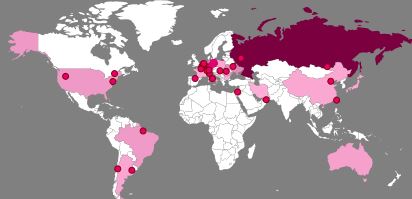
Deutsche Telecom Tracks Global Cyber Attacks In Real-Time
We all know that cyber attacks are incredibly prevalent in the World Wide Web today, but until you see it with your own eyes it’s difficult to grasp just how frequent they really are. In order to raise awareness about how often such attacks occur, German telecommunications firm Deutsche Telecom has just launched a new, ...
Cloud Networking Startup Pertino Wants to Bring SDN to the Masses
Software-defined networking player Pertino has become the latest company in the space to secure the financial muscle to move forward with its plans, raising $20 million in a series B funding round. The company said that the funds will be used to expand its market strategy and service offerings, having previously raised $8.5 million in ...
Carl Icahn Wants To Screw Michael Dell’s Buyout. Or Does He?
Michael Dell could be about to square off against a ruthless new adversary over his proposed buyout of the company that bears his name, with reports suggesting that the infamous corporate raider Carl Icahn is buying up shares in a last-ditch bid to scupper the deal. CNBC reports that Icahn, who has a well-deserved reputation for ...
Hungry Big Data Serves Up A Treat
The rise of Big Data has given the enterprise plenty of food for thought over the last few years, but big business isn’t the only industry that this phenomenon has been eating away at. From the latest trends in restaurant cuisines to food production and safety issues, Big Data is taking a very big bite ...
How Google Makes Money In Mobile… From Everything And Everyone!
It’s no secret that Google’s gotten pretty damn big in mobile. It’s Android platform has conquered the entire world, becoming the most widely used smartphone the planet has ever seen. Android is so big in fact, that there’s speculation China might even be planning to take action to prevent it from strengthening its grip on ...
Google Owns Up To FBI’s Warrantless Data Requests
Google has taken another step towards greater transparency with the revelation that the FBI made ‘up to’ 1,000 requests a year for user data from 2009 to 2012, using a controversial and secretive technique known as a “National Security Letter,” that does away with the need for an arrest warrant. For those who haven’t heard ...
EU Fines Microsoft $732 Million For Browser-Choice Debacle
European Union regulators have just slapped Microsoft with a hefty $732 million fine after it failed to live up to its promise to give millions of Windows users a choice of which internet browser to use upon installing the software for the first time. Microsoft had voluntarily agreed to give European consumers a choice of ...
Is China Planning To Act Over Google’s Android Dominance?
It’s no secret that Google’s Android operating system has become incredibly popular in China over the last couple of years, just as it has in almost every other county, but this might not be the case in future if its government decides to intervene. China’s authorities believe that the country is way too reliant on Android, ...
Healthy Big Data: Just What The Doctor Ordered
Big Data is creating a lot of buzz in the healthcare industry these days, but are our hospitals really ready for such a radical overhaul of the way they go about fighting diseases and saving lives? Some of the largest healthcare organizations in the country undoubtedly are, but there’s also no question that smaller to mid-sized ...