Nico Popp
Latest from Nico Popp
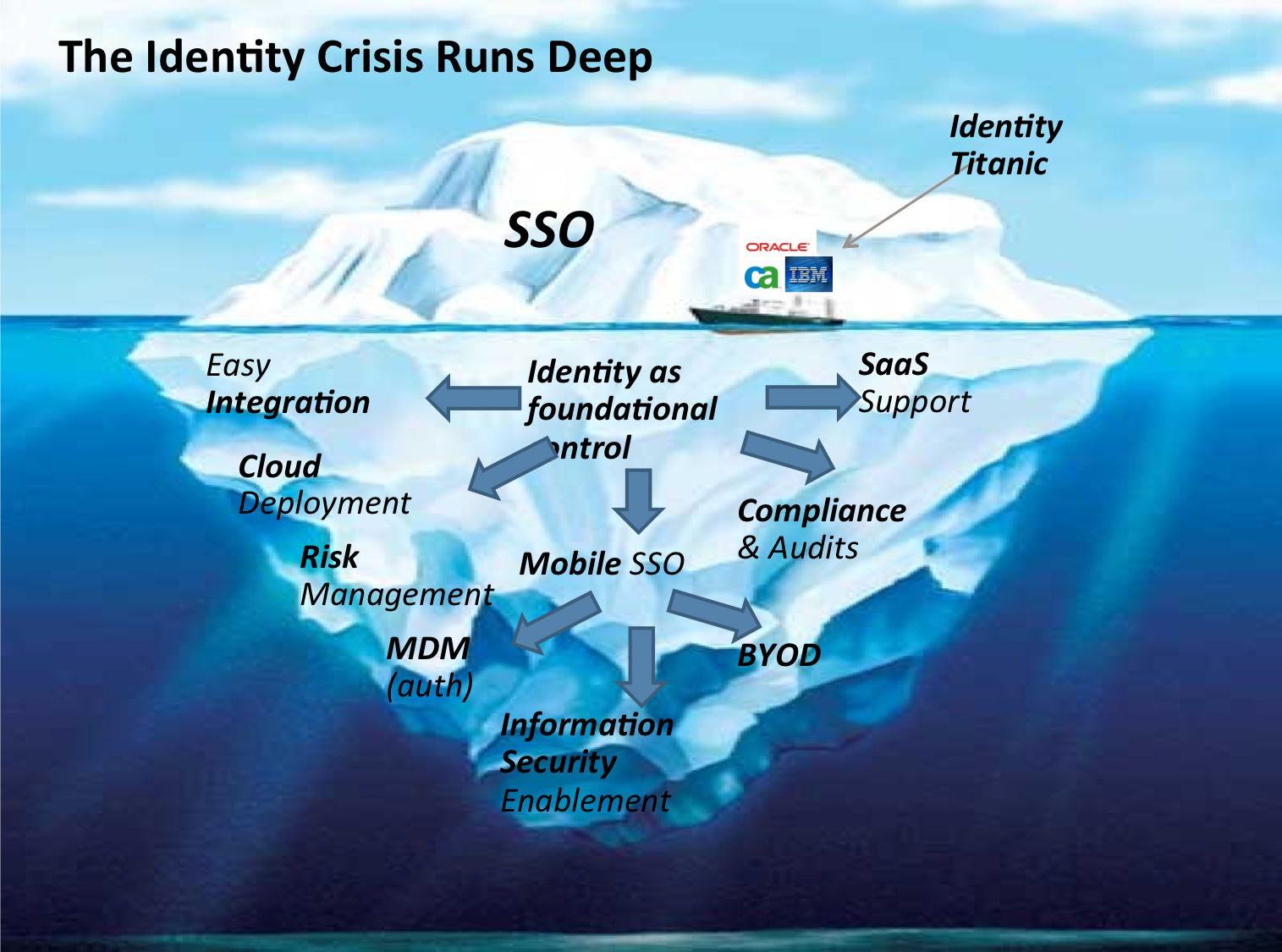
The Future of I.T. – Cloud, Mobile, and the Identity Iceberg
It is a fun time to be in I.T since pretty much everything is changing under disruptive new technology trends. The world of identity is not indifferent to this change. New IT technology platforms such as cloud, mobile, and social are already impacting the way modern enterprises manage identities. Indeed, these changes are profound and ...
The Four Horsemen of Cloud Brokering
The concept of cloud brokering had been drawing more attention lately. In particular, Gartner has developed quite a bit of market analysis on the topic. Most of these analyses tend to focus on the business of cloud brokering. However, I find it insightful to consider the potential technology platforms associated with cloud brokering. Very often, ...
The Perimeter is Dead, Long Live the Cloud Firewall
We are announcing Symantec O3 early access program, a new approach to securing enterprise clouds. But what is Symantec O3 really about? No doubt, cloud is an inexorableIT trend. However, CIOs and CISOs often cite security as a major concern. That is not to say that the new cloud platforms are fundamentally more insecure than ...
Why Mobile and Cloud Security Eventually Converge
The two hottest areas in enterprise security are undeniably mobile and cloud. As small and large security companies go after the fast growing markets, few seems to understand that both markets will rapidly converge to be serviced through a single solution. Yet, it should Beyond the simple fact that mobile is about the cloud and ...
From Windows to the Cloud: “Nothing is created, nothing is destroyed, everything transforms.”
Every so often in technology, new trends emerge to drive large changes to society by transforming our established computing paradigms. Cloud as a computing pattern is certainly not dissimilar. The cloud carries in itself all the genes of disruption that the PC, client-server and Web revolutions embodied before it. For many, cloud computing is the ...
Needed Right Now: A Baseline for Cloud Security and Trust
For most enterprise and security vendors, the cloud is fascinating both as a technology and a business disruptor. In fact, SAAS CEOs such as Successfactor, SalesForce and NetSuite are hot shots in Silicon Valley these days. Yet, most of us are still wondering how much IT budget is actually going to be thrown at the ...
Federation is the Key to an Open Cloud
This week is the week of the OpenID summit in Mountain View, California. We are all hoping that 2010 will be another pivotal year for open identity. There seems to be a combination of market forces that are making federated identity more attractive. In fact, we are hearing new compelling use cases for federation. A ...
Why the World Could Go M.A.D. [Google and China]
As the world already knows, Google and a few other prominent US companies got severely hacked around Christmas time last year. Sophos has an interesting analysis of the exploit. Web malware and a zero day vulnerability in IE6 were essential to the exploit. For security folks, this was a meaningful event. The level of sophistication ...
The Inexorable Convergence of Cloud and Security Services
Concerns for the security of application run in the cloud are running high. The perceived lack of security of cloud platforms is often cited as the primary obstacle to adoption. Whether "cloud" is defined as infrastructure as a service (storage and compute services ala Amazon), platform as a service (application deployment environment ala Google App ...
Trust assurance in open identity networks
One of key challenges in federated authentication network is the establishment of trust between an identity provider (IDP or OP) and relying party websites (RP). In the real world, contractual agreements provide a simple out-of-band mechanism to effectively bind two parties into a trust relationship. When it comes to federated identity networks, peer to peer ...