Saroj Kar
Latest from Saroj Kar
Microsoft is Getting Ready for Kinect-Controlled Windows PCs
Microsoft continues to support the SDK for developing applications that allow users to connect the Kinect with a regular PC computer, and now Microsoft has revealed a way to use Kinect for gesture-based navigation with Windows. Microsoft’s research department at Research labs in Cambridge demoed a prototype gesture-controlled PC using an augmented version of its ...
Plutora Updates Enterprise Release Manager Platform to Improve Your Software Release Management
The ability to trigger the deployment, the ability to track release management capabilities, and the ability to successfully repeat this process to deploy continuous software releases is a cumbersome process for any IT administrator. The release cycle determines how often software is released into production, how much nonfunctional testing is needed, and how long it ...
Oracle OpenWorld DevOps Round Up: Automation is Needed in Key Areas of IT Innovation | #oow13
Open source plays a key role in IT innovation strategy this year and it’s obvious from watching Oracle do its thing. In fact, Recent years have seen the emergence of a system in which the open source and free software are keeping innovation in IT world. This system takes root in some large web companies ...
Alternative Cloud-Hosting Sites Offering Migration to Nirvanix Users After Its Closure
Last week, San Jose, California based Nirvanix caught the industry by surprise when it announced it was shutting down its cloud services. The company has given short notice to its customers so that they can retrieve their data and move it to some other cloud service provider. Nirvanix has told customers they must stop replicating ...
Weatherproofing The Data Center: Early Innovators Look for Warning Protection Systems
Today you can find data centers in the most unusual places, from an old military base at the South Pole to a Spanish chapel. McMurdo is a scientific research center for the U.S. and it’s located at the South Pole, ideal to keep data center cooling. An old Japanese coal mine, 100 meters underground, is ...
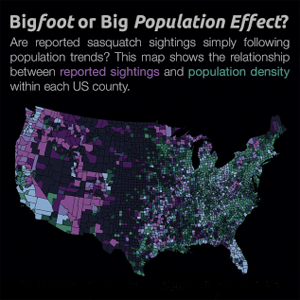
Looking for Bigfoot with Big Data? Infographic Shows 3,313 Sightings of Bigfoot in Last Century
Big Data have been used to explore a range of unusual items, but the latest research might be a unique on its own – the hunt for Sasquatch. Josh Stevens, a PhD candidate at Penn State University, has compiled 92 years worth of data on Bigfoot, exhibiting where the legendary creature has reportedly been wandering ...
ZeroTurnaround Productivity Report: Developers Look for Possible Correlation Between the Methods and Tools
Like other businesses, developers spend only part of their time with their core process, namely writing code. Productivity suffers from continual interruptions, and time is lost spent solving problems, developing documentation, testing, and producing reports. The observations above were revealed as part of the 2012 edition of ZeroTurnaround Productivity Report. Developers spend much of their ...
Sauce Labs Launches BrowserSwarm in Partnership with Microsoft, appendTo For Testing Apps in the Cloud
The demand for development and testing tools in the cloud-based applications is exploding. As the world becomes more mobile and online interactions increasingly move to specialized applications, it’s increasingly important that these apps perform and meet consumer demands. Originally launched to support Selenium tests in the cloud, Sauce Labs has expanded to include manual testing, ...
With SteamOS Valve is Bringing Linux in Your Living Room
Valve has taken a further step forward to bring Steam to Linux and especially to the living room. To make this happen, the company announced SteamOS, a proprietary operating system built around the Linux world that will bring its popular front-end store gaming and entertainment software to living room computers, allowing Valve to indirectly enter the ...
Youth Cyber Crimes on the Rise, but How Ready Are We?
Hackers are becoming more and more creative in their efforts to sneak into users’ computers and infect them. Many of those caught for cyber offences belong to the younger generation. Most motives behind the crimes include making quick money, sexual harassment, playing pranks, causing mayhem, taking revenge, and extortion. It is most worrying that these ...