 NEWS
NEWS
 NEWS
NEWS
 NEWS
NEWS
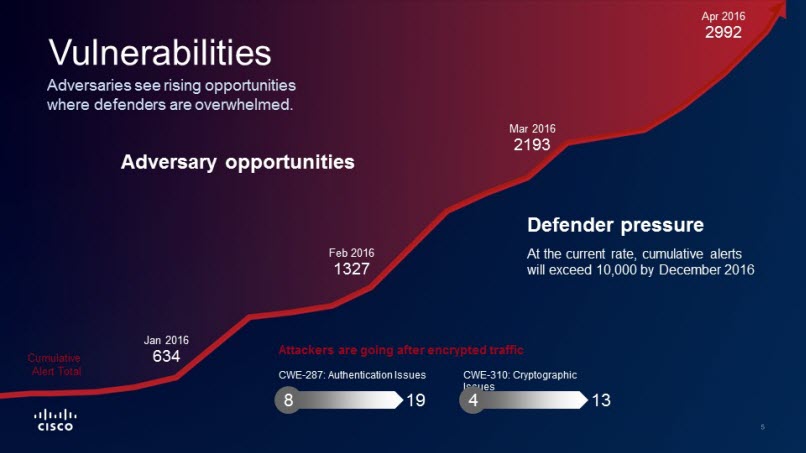
Cisco Systems Inc.’s 2016 Midyear Cybersecurity Report, which was released today, paints an alarming picture of the state of security defenses, even as attacks proliferate and get more sophisticated and ruthless. The report, which is based upon data gathered from Cisco’s global network, depicts a mish-mash of outdated and unpatched software offering up tempting targets to attackers who move with ever-improving agility and precision.
The mid-term report focuses in particular on ransomware, a relatively new threat in which attackers hold victims’ machines hostage unless a ransom is paid. Lucrative returns and multiple points of entry could make this attack “far more prevalent,” researchers conclude. Ransomware “has evolved to become the most profitable malware type in history – and businesses are now becoming a target of choice for some ransomware operators,” the study says.
Cisco calls the new breed of this kind of attack “Ransomware 2.0.” It’s self propagating, resilient and quick to spread. “It’ll move through an organization to find high-value assets and then strike,” said Jason Brvenik, principal engineer in Cisco’s Security Business Group. “The adversary is clearly managing a business and looking to increase their market.”
Most ransomware threats today can be foiled with good backup, but that may not be the case for long. “Future ransomware attacks will evade detection by being able to limit CPU usage and refrain from command-and-control actions,” the report says. “These new ransomware strains will spread faster and self-replicate within organizations before coordinating ransom activities.” Backup continues to be the best defense in the meantime.
Attackers are also increasingly targeting Adobe Flash vulnerabilities, which were responsible for 80% of successful exploit attempts by users of the Nuclear exploit kit. The popular JBoss middleware is another prime attack vector, with 10% of successful ransomware attacks exploiting vulnerabilities there. Many attackers use “JexBoss,” an open-source tool for testing and exploiting JBoss application servers and an example of the way in which miscreants increasingly cooperate and share each other’s handiwork, with some even selling their services. “Many of the JBoss vulnerabilities used to compromise these systems were identified five years ago, meaning that basic patching and vendor updates could have easily prevented such attacks,” the report says.
Echoing the findings of many other studies, Cisco researchers say failure to apply basic standards of software maintenance are one of the biggest risk factors for potential victims. An analysis of 103,121 Cisco devices connected to the Internet found that:
Crooks are also turning their attention back to servers after having focused their attention on clients for the past several years. Clients are an easier target to strike, but servers offer a bigger payoff as known exploits continue to go unpatched. “They’re seeing that servers are easy to attack and can compromise hundreds of users instead of a few,” Brvenik said. “They’ve learned that once inside a network the attack is pretty easy to carry out.”
An increasingly popular tactic is to penetrate a server, and then lie in wait, stealing small amounts of information over a long period of time. Attackers also embed themselves in compromised servers and then spread out laterally through the network. SANS Institute reported in 2014 that the average exploit goes undetected for 312 days.
Attackers now also frequently use encryption. Cisco detected a 300% increase in the use of the HTTPS protocol by malware distributors over the past four months. A growing number of samples also showed evidence of use of the Transport Layer Security (TLS) network encryption protocol. “This is a cause for concern among security professionals, since [TLS use] makes deep-packet inspection ineffective as a security tool,” the report says.
Businesses are also increasingly using encryption to scramble data and render it useless to thieves, but there are vulnerabilities in even the best encryption schemes researchers say. “If encryption isn’t done properly, it’s not providing protection,” the report notes. In particular, unencrypted hand-off points, bad certificates and VMware vulnerabilities may enables attackers to gain access to keys. “Many think they have a secure connection, when in reality they don’t,” Brvenik said.
The best protection against attack continues to be paying attention to the basics. The report recommends the following steps.
In the final analysis, though, businesses are on the defensive. “The attacker only has to be successful once,” Brvenik said. “The defender has to be successful every time.”
THANK YOU