 INFRA
INFRA
 INFRA
INFRA
 INFRA
INFRA
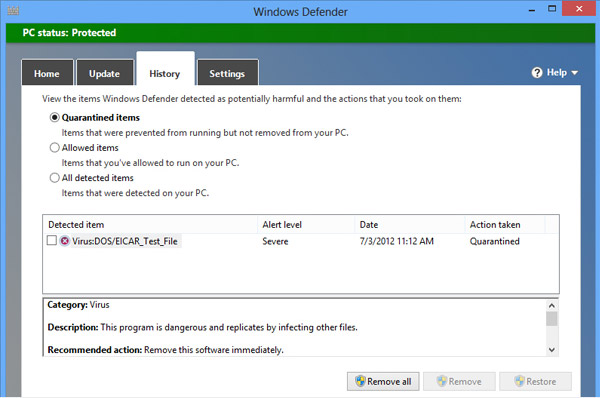
Microsoft Corp. has patched a security vulnerability described as “worst Windows remote code exec in recent memory” that potentially allowed malicious actors to install malware via Microsoft’s anti-malware software.
Those tools, of course, are meant to prevent malware being installed on the market-leading operating system. The vulnerability was discovered by Google Inc. Project Zero researcher Tavis Ormandy, who as well as describing the flaw in negative terms also added, “This is crazy bad.”
According to Ormandy, the vulnerability, which could be found in a wide range of various Microsoft products, was caused by the software not properly scanning files. That in turn could lead to memory corruption on computer systems. All modern versions of Windows, including Windows 8, 8.1 and 10 and Windows Server 2012, are at risk since the software is turned on by default.
The vulnerability, called CVE-2017-0290, allows attackers to create files that can install malware while the affected software is examining files. Worse, given that the software runs with administrative privileges, the malware would have free rein to do what it likes on a targeted Windows installation.
“There are many ways that an attacker could place a specially crafted file in a location that is scanned by the Microsoft Malware Protection Engine,” Microsoft said in a security advisory. “An attacker who successfully exploited this vulnerability could execute arbitrary code in the security context of the LocalSystem account and take control of the system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.”
Microsoft added that there was no evidence that the vulnerability had been exploited by attackers.
Windows users are not required to do anything in terms of updating their software. The updates are being automatically pushed out to the range of affected software titles.
Support our open free content by sharing and engaging with our content and community.
Where Technology Leaders Connect, Share Intelligence & Create Opportunities
SiliconANGLE Media is a recognized leader in digital media innovation serving innovative audiences and brands, bringing together cutting-edge technology, influential content, strategic insights and real-time audience engagement. As the parent company of SiliconANGLE, theCUBE Network, theCUBE Research, CUBE365, theCUBE AI and theCUBE SuperStudios — such as those established in Silicon Valley and the New York Stock Exchange (NYSE) — SiliconANGLE Media operates at the intersection of media, technology, and AI. .
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a powerful ecosystem of industry-leading digital media brands, with a reach of 15+ million elite tech professionals. The company’s new, proprietary theCUBE AI Video cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.