 NEWS
NEWS
 NEWS
NEWS
 NEWS
NEWS
Apple’s reputation of providing platforms that are impervious, or close thereto, to malicious attacks has taken another slight battering with an exploit found in its OS X operating system that allows for the installation of malicious code.
The newly discovered exploit takes advantage of a flaw in OS X’s “Gatekeeper” feature, which verifies that software being installed on an Apple Mac is safe to do so.
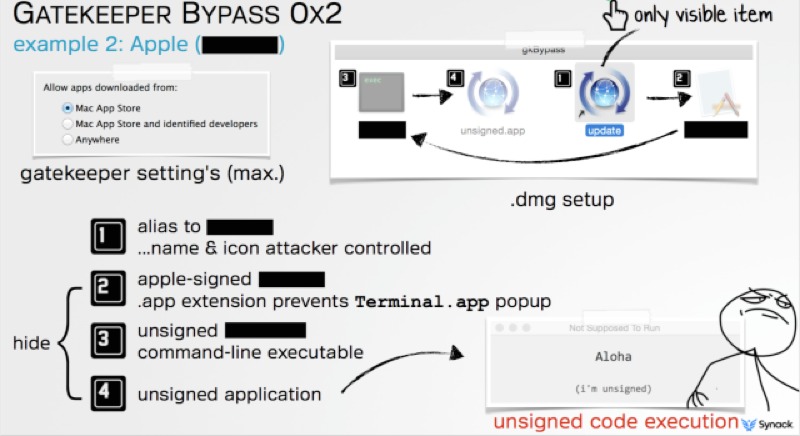
Patrick Wardle, Director of Research of security firm Synack, Inc. discovered the exploit, which as he explained to Ars Technica uses a binary file already trusted by Apple to pass through Gatekeeper; once the trusted file passes through the Gatekeeper security check it is said to execute one or more malicious files that can install a variety of programs including password loggers, botnet software, and other forms of nefarious things.
“It’s not super complicated, but it effectively completely bypasses Gatekeeper,” Wardle explained. “This provides hackers the ability to go back to their old tricks of infecting users via Trojans, rogue AV scams or infect applications on Pirate Bay.”
Noting that the risks are more than the occasional stray user, Wardle added that “more worrisome to me is this would allow more sophisticated adversaries to have network access…Nation states with higher level access, they see insecure downloads, they can swap in this legitimate Apple binary and this malicious binary as well and man-in-the-middle the attack and Gatekeeper won’t protect users from it anymore.”
Implementing the exploit is simply a matter of changing the name of one binary file to another:
[The] exploit works by renaming Binary A but otherwise making no other changes to it. He then packages it inside an Apple disk image. Because the renamed Binary A is a known file signed by Apple, it will immediately be approved by Gatekeeper and be executed by OS X.
From there, Binary A will look for Binary B located in the same folder, which in this case is the downloaded disk image. Since Gatekeeper checks only the original file an end user clicks on, Wardle’s exploit swaps out the legitimate Binary B with a malicious one and bundles it in the same disk image under the same file name. Binary B needs no digital certificate to run, so it can install anything the attacker wants.
Wardle claims to have informed Apple of the vulnerability 60 days ago with the tech giant yet to issue a patch for it, although it is believed a patch is currently being worked; it could be some time off, as the patch is said to require a number of serious changes to the OS X code base.
The vulnerability is believed to apply to all versions of OS X since 2012 which use Gatekeeper to verify installs.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.