 INFRA
INFRA
 INFRA
INFRA
 INFRA
INFRA
Researchers at Cisco Systems Inc.’s Talos threat research group have published a report on a scary new form of malware that’s difficult to detect.
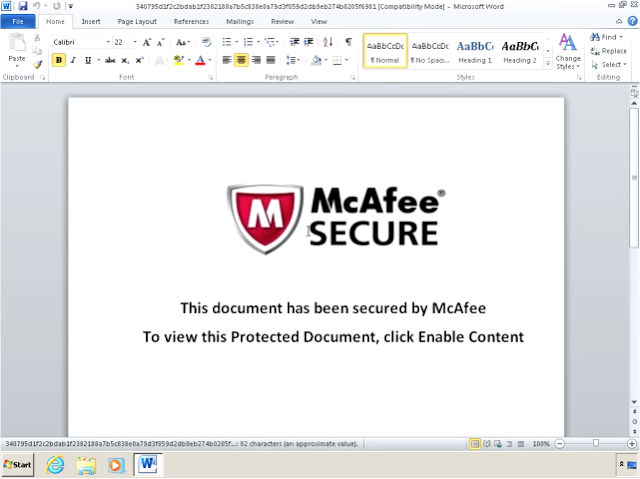
Dubbed DNSMessenger, the malware uses Microsoft PowerShell scripts to hide itself and connect directly with a server using a victim’s Domain Name Service port. It’s distributed as a Microsoft Word document spread through a phishing campaign, which attempts to appear like a known or reputable source.
Once opened, the file pretends to be a protected document secured by McAfee Security and asks the user to once again click to view the content that was supposedly in the original file. Not surprisingly, there’s no content in the file and the second click instead executes the malicious script in the file, eventually leading to the victim’s computer being compromised.
But that’s where the similarities with usual malware ends. Instead of writing the malicious code to the victim’s hard drive, the malware does everything in memory instead, making it difficult to detect. A second stage is stored in the Alternate Data Stream with the NTFS (standard Windows) file system or directly inside the registry, while a third-stage PowerShell script establishes communications with a command-and-control server via DNS. A DNS service is usually used to look up the Internet Protocol addresses associated with domain names, but in this case it is used to pass text messages instead.
What isn’t clear is exactly what sort of malicious commands the hackers are using the DNS backdoor to execute. “We were unable to get the C2 (command and control) infrastructure to issue us commands during our testing,” the Talos team said in a blog post Thursday. “Given the targeted nature of this attack, it is likely that the attackers would only issue active C2 commands to their intended target.”
While HTTP and HTTPS gateways are regularly monitored by networks, the same can’t be said for DNS, and the hackers are well aware of this.
“This malware sample is a great example of the length attackers are willing to go to stay undetected while operating within the environments that they are targeting,” the Talos team added. “It also illustrates the importance that in addition to inspecting and filtering network protocols such as HTTP/HTTPS, SMTP/POP3, etc. DNS traffic within corporate networks should also be considered a channel that an attacker can use to implement a fully functional, bidirectional C2 infrastructure.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.