 INFRA
INFRA
 INFRA
INFRA
 INFRA
INFRA
Researchers at Kaspersky Labs have detailed a possibly state-sponsored “Advanced Persistent Threat” malware campaign that has gone under the radar for six years before being detected.
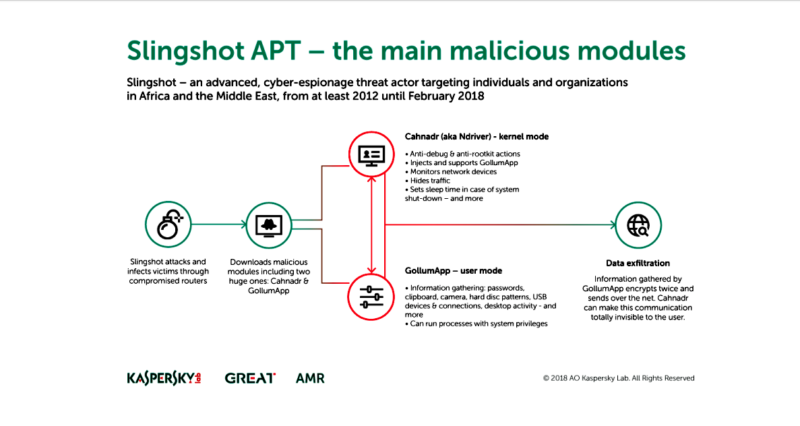
Dubbed “Slingshot” due to the use of the name in the primary malware code, the APT campaign, revealed Friday, is believed to have been operating since 2012 without being noticed. The malware, which resides in routers made by Latvian hardware maker MikroTik, likely wasn’t detected before now because routers are usually only accessed by IT staff in an enterprise environment.
Despite its discovery, the researchers themselves don’t know how the malware spreads. The initial part of the attack replaces a dynamic link library file on a given router with a malicious one, which then targets any computer connected to the router by targeting its memory when the user runs Winbox Loader software — software used by Mikrotik router users.
Once that occurs, the computer connects to a remote server to download the primary Slingshot malware. That malware consists of two modules, Cahnadr and GollumApp, both of which facilitate data theft.
“Running in kernel mode, Cahnadr gives attackers complete control, without any limitations, over the infected computer,” Kaspersky explained. “Furthermore, unlike the majority of malware that tries to work in kernel mode, it can execute code without causing a blue screen. The second module, GollumApp, is even more sophisticated. It contains nearly 1,500 user-code functions.”
So far Slingshot has only been detected in MikroTik routers, but the researchers noted that the methodology could easily be applied to other brands of routers as well.
“I’ve never seen this attack vector before, first hack the router and then go for sysadmin,” Costin Raiu, Kaspersky’s director of global research and analysis, told The Register. “We’ve seen a lot of attacks against sysadmins but sometimes it’s tricky to find them. This is a very good way to hack the sysadmin and get the keys to the kingdom – it’s a completely new strategy.”
Kaspersky recommended that MikroTik users should make sure they are running both the latest versions of the router firmware as well as the WinBox managing software.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.