 INFRA
INFRA
 INFRA
INFRA
 INFRA
INFRA
The ransomware that swept across the world Friday remains a huge threat after all, despite media reports over the weekend that claimed a security researcher had “accidentally” managed to put a stop to the widespread WannaCry ransomware.
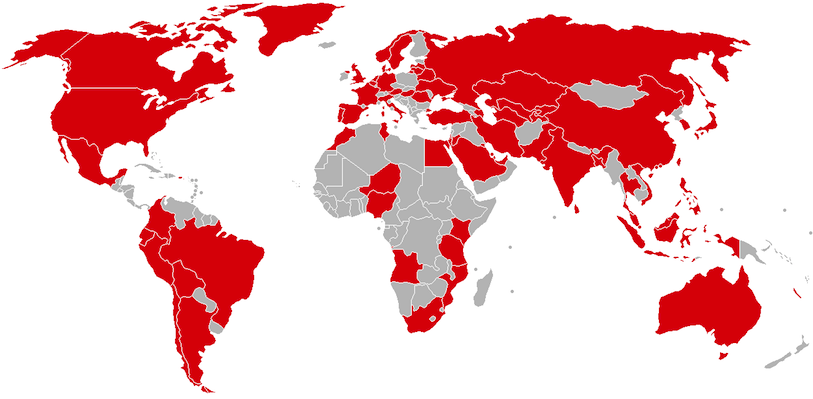
Indeed, according to many reports, the malware has continued to evolve and is expected to infect millions more computers and organizations as business is set to open across the globe Monday, perhaps beyond the countries already infected (pictured).
The new versions of WannaCry, of which there is more than one, are believed to have been created by a combination of the hackers behind the original ransomware campaign amending the code along with a number of copycat hackers developing their own variations. The code used by WannaCry to hijack Windows machines is based on Eternal Blue, a Windows hacking method developed by the U.S. National Security Agency that was published online by hacking group The Shadow Brokers in April. That means the methodology behind the malware is easily accessible.
According to reports, the original version on WannaCry, also known by the names of “WanaCypt0r” and “Wanna Decryptor,” managed to raise at least $28,000 in bitcoin ransom payments, although that figure related only to the original bitcoin wallets used in the first version of the malware Newer versions used a wider variety of payment addresses.
Not surprisingly, given the level of media attention WannaCry has achieved across the globe, governments have been forced to take unprecedented action. U.S. President Donald J. Trump has ordered Homeland Security Adviser Thomas P. Bossert to coordinate a series of government responses to the attack. In addition to developing countermeasures to the malware, they will also search for those behind the ransomware attack.
Countries including India and The Philippines have also established task forces to deal with WannaCry’s spread, while the cybersecurity advisor to the Australian Prime Minister warned that “unfortunately, there are some very smart and bad people out there who spend their times trying to make things worse for us, and this is not game over for us.”
Paul Kurtz, founder and chief executive officer of the security firm TruSTAR Technology Inc. told SiliconANGLE that the spread of WannaCry shows that there’s an ongoing weakness when it comes to current cybersecurity measures.
“The playbook for creating new ransomware campaigns has been written and everyone is following it,” Kurtz said. “Ransomware campaigns often rely on an easy-to-buy RIG exploit kits, and then they are combining it with ransomware like WannaCry, Cerber and Locky.”
Kurtz said that a “sector-specific approach” to cybersecurity is no longer sufficient. “We now have ample proof of commodity ransomware being used against multiple sectors of the economy within a 24-hour period,” he said. “This is what we’ve all feared but never seen.”
Computer users are advised to make sure their Windows installations are up to date. They also should not open attachments on emails from unknown sources, given that WannaCry is primarily being spread by a co-ordinated phishing campaign that seeks to fool people into thinking an attachment is from someone they know.
THANK YOU