 INFRA
INFRA
 INFRA
INFRA
 INFRA
INFRA
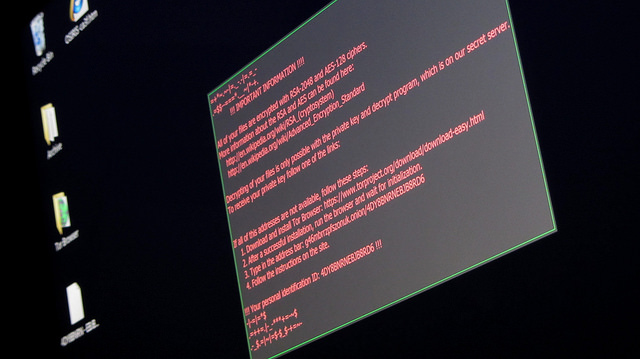
A ransomware attack targeting the website of the Ukraine Energy and Coal Industry Ministry could be a sign of more nefarious attacks ahead, according to security industry experts.
The attack, which took place in the early hours of Tuesday morning, involved a message appearing on the website in English demanding a ransom payment in bitcoin in return for a key to gain access to encrypted files on the website server. Signed by a hacker using the name X-Brang, the message demanded 0.1 BTC ($930) and included details on how to make the payment available via a Gmail address.
Reuters reported that the attack appeared to be isolated, quoting officials as saying it was likely part of ongoing Russian attacks against the country, but security researchers believe it could be something more.
“One way to look at it is to not only focus on what was attacked/compromised, but what wasn’t and whether this was a probing attack for something more serious,” David Ginsburg, vice president of marketing at Cavirin Systems Inc., told SiliconANGLE. “For example, looking for credentials and such that could lead to additional attacks against the grid itself, much like that which occurred in 2016. Even in the U.S., there is a growing awareness of the vulnerability of the grid, evidenced by action within Congress such as the Securing Energy Infrastructure Act and others, and even calls for nondigital overrides.”
Joseph Carson, chief security scientist at Thycotic Software Ltd., said he believes the ransomware attack is another example of cyberattack misdirection. “The main goal of this ransomware stems not only from financial motivation, but more of a statement. However, it is not exactly clear if it was a political motive or simply hacktivism.”
Carson added that the attack is “clearly multiple cyber actors, possibly working together” or at least in communication with each other. “It’s very likely that the cybercriminals behind this recent cyberattack against the Ukrainian Energy Ministry are testing their new skills in order to improve for a bigger cyberattack later or to get acceptance into a new underground cyber group that requires showing a display of skills and ability,” he said.
Not everyone agrees with that proposition, however. James Lerud, head of the Behavioural Research Team at Verodin Inc., said that “it appears that this attack was from someone (or a group) who uses automation to mass scan and then compromise vulnerable websites with ransomware.”
Furthermore, he said, “it is likely that the operators of this did not know that they were going to compromise this website going into it. Looking at cached versions of the website, it appears that the site was using Drupal 7. The presence of artifacts that give away what code they are running could suggest that the website administrators did not go out of their way to lock down the site.” In addition, he noted, Drupal 7 also had a massive vulnerability known as “Drupalgeddon 2” announced March 28. “If the website owners did not patch it, it is entirely possible this is how the ransomware got in.”
THANK YOU