 INFRA
INFRA
 INFRA
INFRA
 INFRA
INFRA
A newly discovered flaw in the way Android stores data allows hackers to use external storage as a way to access data, according to new research published today.
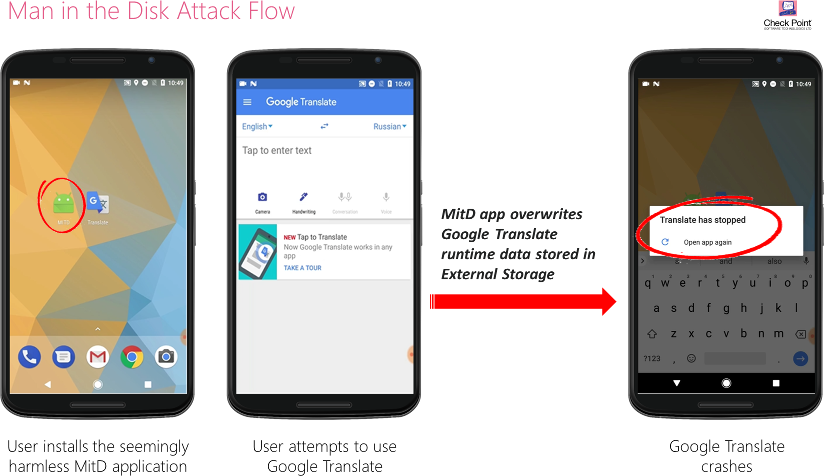
Discovered by security researchers at Check Point Software Technologies Ltd., the hack vector, a so-called “man-in-the-disk” attack, takes advantage of careless Android app security when dealing with external storage connected to an Android device.
That access may allow a hacker to undertake a number of “undesired outcomes,” such as silent installation of unrequested, potentially malicious, apps to the user’s phone, denial-of-service for legitimate apps, and even crashing applications. All those could open the door to possible injection of code that would then run in the privileged context of the attacked application.
External storage for the purposes of the hack vector means storage that is not covered and segregated by Android Sandbox and can mean both an SD card or a partition within a given device’s storage that can be accessed by all applications. External storage is often used for media storage and can also be used by developers for additional app storage and processing, the latter being where the problems occur.
“We have witnessed cases where an app was downloaded, updated or received data from the app provider’s server, which passed through the external storage before being sent on to the app itself,” Check Point explained. “Such practice offers an opportunity for an adversary to manipulate the data held in the external storage before the app reads it again.”
Tapping into the external storage is said to be relatively easy and can occur through the use of a malicious app disguised as something else that contains the attack’s exploit script. Then the attacker can monitor data transferred between any other app on the user’s device and the external storage and overwrite it with their own data.
Although one might presume the implementation of careless security in using external storage would be introduced by third-party developers, the researchers even found apps designed by Google LLC, including Translate and Voice Typing, that introduced the same vulnerability.
The researchers concluded that Android app development guidelines already specify avoiding the use of external storage in this way. Given that the advice is seemingly ignored, another solution is required.
“It would seem that mere guidelines are not enough for OS vendors to exonerate themselves of all responsibility for what is designed by app developers,” they noted. “Instead, securing the underlying OS is the only long-term solution to protecting against this new attack surface uncovered by our research.”
THANK YOU